created: 2024-06-23T14:57:42
updated: 2025-07-31T23:43:24
modified: 2026-02-09T07:10:38-06:00
Editor's note: the fool thinks himself cartographer charting five dimensional space-time as if a plane could hold its complexity. Nor does he address its propensity for change where blurry borders shift as swiftly as the dunes and just as unpredictably. Still, it may help the layperson understand their place, insubstantial though it may be. – ANV.
Two toruses surrounding a sphere with all of them bleeding into one another, gradually becoming each other.
🜁🜂🜃🜄
Our universe, all of reality as we can objectively experience it and study it, is but one level of a greater existence. We occupy a world of three spatial dimensions and one of time. The two are interlinked and influence each other such that we call the whole thing space-time. The only real difference between time and space is that time moves only in a single direction for us. We can slow it down, even stop it, but we cannot reverse it or travel backwards upon its trajectory. This leads to entropy, the fact that everything we know will one day end.
But there are other places that our minds can reach into given the right circumstances. Some of these are what we might call parallel, some are “above” or “below”, but all are in directions that have no names and that cannot be described easily by science. They are mystical places, magickal realms that require altered states to experience.
Intelligence, sapience, self-awareness are the keys to this type of “travel”. Humans have evolved the capacity for it. Perhaps thanks to genetic coding from our forebearers. Perhaps, given time, all intelligence will develop these abilities.
IMAGES MISSING
The Other Way / The Æther / The Astral Plane
Directly on top of what we can see with our eyes is another place with many names. To see in that space is called looking the Other Way by some or seeing auras. When science wasn't as strong as it is today, everyone believed it was there, just invisible. Today, it is left to the realm of magick and psychics, unfortunately.
Most sapient life can peer into this place with practice. Looking the Other Way is also called opening the third eye but, in truth, it is looking at the world from an impossible angle, orthogonally. Our biology is not designed to understand this strange direction so we have developed a series of sensory metaphors accepted into the universal unconsciousness that allows us to interpret it without going mad.
We see auras and visions, we hear music or discord, we smell flowers or filth, we feel tingling or coldness on our skin, we taste sweetness or other things. It is the way we see a deeper truth about the world around us.
The dead leave their imprint on this place and you may find ghosts or spirits. Do not be fooled by them. They are not the people they represent. They are echoes, imprints, memories of them, but they are not truly living things. Given time, they may believe themselves to be who they seem, but it is a self-deception.
Among the ghosts are things that feed on such energy and things that can feed on our lifeforce directly. To feed, they need to be perceived. But only once. If you see them, smell them, taste them, they can touch you in return and, in touching, attach themselves. From that moment forward, you have a parasite that will suckle itself on your dreams, your hopes, your fears, your tears, any strong emotions, though some seem to have preferences. To remove them, you have to see them once again which, of course, opens you up to more attacks.
There are even fully sapient beings that appear to be native to this place, taking innumerable shapes and having their own drives and desires. They may choose to reach out to us as friends or as predators, but mostly they ignore us as not worth the effort.
There are some humans who can leave their bodies behind, but tethered, and send their essence far out into the Other Way, discovering those temples and cities, graveyards and ruins of all civilizations that came before and where the old gods once resided. The silver cord connecting the wandering soul to the body is thin, nearly invisible, but it is strong as spider silk spun from steel. Strong, but not impervious to damage. If the cord is broken, the traveler must find their own way home. If they have gone far enough, this may be impossible, leaving their body without a force to drive it, sleeping dreamlessly, autonomously breathing, digesting, living, but not truly alive. When the body eventually dies, the spirit will feel its loss and it, too, will fade.
The other possibility is you may return to find that your body is no longer yours at all. While absent your body, some opportunistic being may slither inside the hole you left behind. You will become “indwelt” by something that noticed your absence. They will have your body and your mind, more than enough to be you and take over your life. The only thing missing is your soul which, with the loss of the body, will likely fade or be devoured. “You” will cease to be while the thing wearing your skin and remembering your memories is free to experience the physical world for the rest of your lifetime.
Looking the Other Way is difficult and dangerous. For most, it is just a “feeling” or a “knowing” that comes at certain times, nothing as dramatic as auras or ghosts. And, if you have these extra senses? Embrace them, enjoy them, use them, but do not choose to venture further afield unless you are willing to accept the risks.
The Dreaming
The Dreaming is easy to reach. Just go to sleep for 90 minutes or so and your brain reaches out to it automatically. It's the little melting pot of the collective unconscious, where we go to sort through our memories and feelings and give our brains little bit of a workout for the night. It's exercise for your subconscious. It's healthy and natural to be here and everybody does it.
The Dreaming is not designed to be a place that builds memories. Your brain goes out of its way to make the conscious mind forget what it experiences. It is only through luck or practice that we may begin to remember our dreams in detail. And that is the first step to going deeper.
The Dreamlands
The Dreamlands are a little bit deeper. You have to reach the Dreaming first, before you can reach the Dreamlands. You have to find the way. Sometimes, you fall into the Dreamlands by mistake and experience the most amazing, life-changing dreams you've ever felt. Realer than real. Colors with no names, indescribable music, flying and swimming, life affirming, impossible to forget.
But, typically, you have to find your way to the Dreamlands. You have to understand first that you are dreaming, which is more difficult than it sounds. Your brain tries very hard to convince you that your dreams are reality while you are in them because your brain has an agenda. Your brain wants you to learn something or see something and if you realize you are dreaming, you can derail that plan.
If you know you are dreaming, if you are Dreaming, you can push back, gently at first. Learn the rules. Make a few additions.
The next trick is to remember your previous Dreams when you are Dreaming. Remember what you learned last time. Don't be flashy; don't draw attention to it. Just remember. Remember how you could stand on your tip toes and then lift your toes and float in place? See if you can still do that. Remember how you could push your hand through a window like the glass was made of putty? Try that again. Could you breathe underwater? There's a swimming pool, see if you still can. Just for a moment. Just for a second. Not enough to take away from the narrative.
When you remember enough tricks, you can finally find the Dreamlands, the real Dreaming for real Dreamers.
It's like Plato's Cave. You've been Dreaming at the shadows on the wall. Now you get to turn around.
Your brain may try to hold you in place, force you to turn back to the cave wall. It will try to convince you that it still has so much to teach you, that you are safer in the cave. You are, of course, but where's the fun in that?
The Dreamlands is populated by creatures of fantasy and horror, with cities ancient and futuristic, all borne of the Dreaming minds of humanity over the centuries. The Dreamlands are an everchanging place, but they only change at the whim of Dreamers. Dreamers can be as gods here. And if you search far and wide, you will find other gods, even gods whose names you've heard from mythology. In the Dreamlands you can build empires and destroy them, visit the center of the earth or the surface of Mars, talk to shadows, shrink down to an inch and befriend insects, expand to colossal size and have a heart-to-heart with a kaiju. Create whatever you can imagine. The human-like denizens of the Dreamlands revere Dreamers above all else.
The biggest risk of the Dreamlands is that you are no longer alone. Other Dreamers visit the Dreamlands and have their own ideas. The Dreamlands are big enough for everyone but there are some who seek out others to antagonize. Perhaps they get bored. Perhaps they are worried that too many people may find the Dreamlands and they will no longer have their little corner.
It is said that when a Dreamer who frequently traverses the Dreamlands dies, their mind finds itself back there, forever. I have no evidence or experience to back this up one way or another as the Dreamlands are far too large to fully explore.
The Fugue
The Fugue is a strange half-existing place, between slumber, dreaming, and wakefulness. It's often called “sleep paralysis” or “night terrors” but it is more than that. When the body is caught just so between dreaming and being fully awake, you can perceive a place that vibrates at a slightly different frequency. It's such a narrow band that it's easy to miss, but it is full of intelligent life. By appearances, they are creatures of nightmare or denizens of hell, but that is just how they look.
In fact, the residents of the Fugue crave human companionship and it is their overeagerness that led to legends of demons sitting on chests or stealing the life from babies. The Fugue is a cold place and the warmth of mankind is dearly sought after and fought over. But it is only in those moments between when we may see each other properly. And it is not easy to stay when you are on the way in or out.
I suppose we all must pass through the Fugue on the way to the Dreaming and back, but we pass so quickly that we scarcely notice.
For those who understand the Fugue, you can make easy friends with the things living there. Faceless, eyeless, skinless terrors by appearance but kind and friendly if you give them a chance. Some love to chat about our world and get their sustenance by the exchange of ideas. Others find physical contact more directly expedient and will eagerly mount and copulate with anyone who assumes the position, whether on purpose or not. This has led to their negative reputation, but, honestly, it's just how they eat and they have to eat.
Those natives that become truly forgotten sink down into shadow, into the Gloam, to be repurposed.
Those that receive enough love may be elevated to Epicurea and become harbingers of daydreams or sudden insights.
The Fugue is also one way to reach Nuntius, the Realm of Knowledge where the Akashic Records and the Library of Babel can be found. You must pass through Nightmare, Regret, and Longing to reach it from this path and most never find their way through.
Effervescence
Between us and The Gleam.
Realm of meaningless delight.
Insight and questing to the right.
Resignation and acceptance to the left.
Perhaps this is the home of the Fae. The Seelie.
Effluvia
Between us and The Gloam.
Realm of decay.
The Unseelie.
The Gloam
Umbra
The Void
The Gutter
The Gloaming
To reach the Gloam without drugs or heavy meditation is not impossible, but is very unlikely. The Gloam is no-man's land between us and oblivion. The Gloam is a gutter, a shadow of this world. Most people seek to avoid it, pass around it, or through it so quickly that it doesn't matter. Mirror walkers can avoid it, shadow walkers make frequent use of it. Vermin from this world and the Dreaming frequently cross over into the Gloam because it is easy to find food there. It is a place where, unlike the Fugue, our warmth is despised and hated. As such, tiny creatures wandering in to eat and dispose of those bits of us that remain is seen as a benefit, doubly so because their presence unnerves us. Spiders, rats, roaches, snakes, flies, maggots, all of them have negative connotations to most humans. To see them in the dark places just adds to our fear and the things that live in the Gloam feed on fear and despair.
They are called Shadow Things, Shadow People, Shadow Men, a thousand other names. They are sought out by some because they know everything. They know everything because shadows are everywhere and they are always listening.
They know everything and they do not lie. They could lie if they wanted to, but telling the truth generally hurts us more than lying to us, so they tell the truth. And that is the crux of their existence: oracles of truth of the most unfortunate kind, things you'd rather not know. Things you can never forget once told.
You don't have to visit the Gloam to find the Shadows. You can reach out to them in many ways. But offering blood, yours or someone else's is the easiest way. They love it when we spill blood. They love it when we are afraid.
And, remember, they are always listening.
Always.
—
The Gloam is also the home of Naralmtu, the God of Shadows. It is not something to be invoked on a whim and most who know of it never speak its name or write down a word about it. To know it is to be known by it and when the shadows take special interest in you, your life will be filled with cold despair, disappointment, hardship, and loss. There are those that worship it, however. The feed it the lifeblood of sacrificial humans and animals. They feed it their own blood. In exchange for knowledge, in exchange for turning the shadows against their enemies. Some followers know they are being used and drained just as surely as their victims, but they do not care. Temporary power over their finite lifetimes is reward enough for these empty souls.
I know a great deal more about this entity, but to write it down is to further imperil myself.
The Gleam
The Blazing World
Hyperspace
The Gleaming
If you have heard of the “machine elves” then you have heard of the Gleam. Without drugs or a strong will and careful magick, this realm is impossible to comprehend. It is as far as our human minds can reach, to go further is to find nothing that can be described or understood. Do not take that as a challenge. Our bodies, our flesh is simply not capable of experiencing that many special dimensions. To put it another way, there are some directions in which we are unable to see. What would “up” mean to a stick figure living on a piece of paper? It is the same for us. The Gleam is the edge of this space. To our minds, it seems to extend forever in all directions, in colors without names, endlessly folding and unfolding itself, rejuvenating and decaying, being born and dying over and over. That is how our brains interpret the edge of 4 dimensional space-time when we try to peer beyond.
From there, if you can properly direct yourself, you can see the past or the future, you can see what might have been or what could never be. You can relive your favorite moment for eternity in just a few moments.
The machine elves hang out on this barrier to greet travelers. It is in their nature to be jovial and helpful, but also chimeric and mischievous. They appear to us to be made of crystalline lattices shaped into insect-like bodies. Just like their entire realm, they are constantly folding and unfolding, becoming and unbecoming. They can, if they wish, project forms more suited to our senses and sometimes they may. Also, while their native language is one of thought pictures, impressions, and feeling, they can translate their ideas into our speech, though something is lost in the translation and it often sounds like they are talking over themselves, trying to mix various meanings together. Imagine the same conversation in each of your ears but with slightly different wording and at a slightly different pace. Now imagine that times a hundred.
The Gleam is a place of possibilities. That is why most of us seek it. You can see what we can be if we make the best choices and it may inspire you to be a better person. That's what the machine elves want. They want us to be the best versions of ourselves.
A single trip to the Gleam can turn anxiety into ecstasy and depression into hope.
—
A secret about the machine elves that most do not know. They are not the highest lifeforms in their plan of existence. In fact, they are barely more than what we would call bacteria or simple multicellular life. But such is the differences in our levels of reality that even the lowest among them is godlike by comparison. It's also why they are interested in us. We are a sapient species reaching out and we treat them with a level of awe and respect that they cannot find in their own world alone.
They line the “shore” of the “ocean” we swim up through, looking for lights to rescue. When we peak through, they surround us and so we are enlightened.
To meet a higher lifeform from their plane would likely be disastrous to a human mind, like gazing into infinity or a naked singularity.
The Gloam is about inevitably.
The Gleam is about possibility.
Ur
When the nothing became something, yet still before the first vibration, before the first waveform, before the first Planck length had been crossed, there was Ur, The First Place, the Ocean of Creation.
It is just as much a furnace, boiling and churning raw possibilities, recombining them into new things while simultaneously devouring and recycling the old with no care as to which. It has no guiding consciousness, no blueprints or plans, no thoughts of its own to speak of.
It is chance.
It is random.
But it is also eternal.
Given time, moments of apparent order can arise out of chaos. If they are quick and lucky, some few of these moments break free, find the surface, crawl away, and seep into other realms. It is from those stolen remnants that everything we know to exist arose.
The borders of Ur are filled with rotting carcasses of failed escapees and the trails, some wide and ragged, some so small as to be invisible, from those that made it. Be wary of stragglers or new arrivals who, eager for energy or ignorant of their strength, may seek you out and do you harm.
Under no circumstances should any living thing deign to enter Ur itself. It's driving nuclear engine would rip apart anyone or anything foolish enough to slip under its surface faster than the speed of light.
It is said that certain creatures, those acquainted with chaos, know ways to traverse the waters safely, but they are known to traffic in lies and half-truths. To put your faith in anything they offer in regards to Ur is more suicidal than simply foolish.
Why would anyone seek out such a place?
Change is seductive, to be someone else, to be better.
Perhaps you are terminally ill.
Perhaps you are hopeless.
Perhaps you are stuck, broken, lonely, inadequate, afraid, incomplete.
Would you be willing to throw your life into a blender and pray you retain your “self” in the recombination?
Would you be so unsatisfied with your current life that you are willing to risk complete dissolution?
Or perhaps.
Perhaps.
You prefer to be undone.
There are those who have been so traumatized by the act of living in the world as it is that they wish to escape into emptiness and leave nothing behind. They do not care for legacies. They do not see “the future” as anything but a continual slide into pain, isolation, and loneliness. They see the truth: entropy is inevitable.
But instead of seeking strength or fellowship, they choose to forget and to be forgotten.
What they do not understand is that Ur is rebirth. They will cease, but every bit of everything that made them who they were will be repurposed and reused to make another or billions of others stretched and threaded until unrecognizable.
True endings are only available from embracing Oblivion, from the orthogonal path back to the beginning, back to the ending. Only there can everything be truly nothing, forever and ever.
—
Nessianna Inmenna operates out of Ur. To her, the radioactive waters are like a warm bath, a comfort.
Elysium / Nirvana
Imagine a party that never ends spanning worlds filled with abundant life. That is Elysium, also called Nirvana.
A “party” is something with a different definition for each culture. For some it is a celebration of excess. For others, it may be an acknowledgement that you finally understand that you have no desires at all. For both, it is a place without responsibilities.
Elysium is a paradise of wanting and needing nothing, whether this is because everything is provided that you could possibly want or a place of emptiness because all worldly concerns have vanished, you will find it here and you will be at peace.
Epicurea
Epicurea is another world of plenty, but it does not give those who visit anything for free. You must work to find what you desire, but it is here. It is always here and you may find it if you pass the tests, survive the gauntlets, answer the riddles. It is a plane of growth and perseverance.
Unlike Elysium, here, you can fail. You may not solve the puzzles on the first try. You may not find your way through the maze. But you can try again.
Hell
Hell is not a place intended for punishment, not directly. Hell is a place for refinement and growth. Some who find themselves here may never realize that and they may be “tortured” for eternity. Others may thrive, find themselves, rarified, and leave freely as something greater than what arrived.
Hell is not a single place or a single experience. It is something that builds itself around the expectations of its inhabitants. Many may share the same Hell or Hells, but that is a quirk of organized religion planting the same set of expectations in the minds of billions.
Nuntius
Nuntius is a realm of secrets, of knowledge, of every book that could ever be written. It is also a plane full of lies and deception so the traveler must be cautious and careful.
One can find the Akashic Record here, but there is no helpful librarian, no card catalog or directory, and any one book is just as likely to be a fake as to be genuine. Additionally, a single wrong step and you may find yourself in the The Library of Babel instead and that path is guaranteed madness.
Vitrium
Imagine a world where every tree, every insect, every blade of grass, every gust of air is broadcasting every detail of itself to every other thing, all the time. It is a world of perfect, unfiltered information; a place where there are no secrets.
To visit Vitrium is to be laid bare to yourself and everyone else. There are no shadow selves here, no lies or deception, only Truth.
For a human mind, the raw experience of such a place is a meaningless cacophony, too wide, too deep, too bright, too loud. It is impossible to process.
Acceptance / Obsequium
Obedience, Submission, Compliance, Resignation
Concerned with how
Science, Religion, Rules, anything with codified and definitive answers, anything that replaces warm hope with cold truth.
Passive while appearing Active.
Insight / Consilium
Insight, Discernment, Understanding
Concerned with why
Introspection, Mindfulness, experience over explanation, seeing and being over knowing.
Active while appearing Passive.
Addendum 1: Oblivion
The Blight
Singularity
Nowhere
Nowhen
Absolute Zero
Before existence, there was Oblivion. Eternal because time had not yet ticked its first. Limitless because space had not yet been borne. It was nothing and everything. Potential without ignition, less than the sum of its parts. It is absolute entropy and the state to which every universe seeks to return.
Naralmtu serve The Blight.
Absolute Zero
https://en.wikipedia.org/wiki/Absolute_zero
Absolute zero is the lowest possible temperature, a state at which a system's internal energy, and in ideal cases entropy, reach their minimum values. The Kelvin scale is defined so that absolute zero is 0 K, equivalent to −273.15 °C on the Celsius scale,[1][2] and −459.67 °F on the Fahrenheit scale.[3] The Kelvin and Rankine temperature scales set their zero points at absolute zero by design. This limit can be estimated by extrapolating the ideal gas law to the temperature at which the volume or pressure of a classical gas becomes zero.
At absolute zero, there is no thermal motion. However, due to quantum effects, the particles still exhibit minimal motion mandated by the Heisenberg uncertainty principle and, for a system of fermions, the Pauli exclusion principle. Even if absolute zero could be achieved, this residual quantum motion would persist.
Although absolute zero can be approached, it cannot be reached. Some isentropic processes, such as adiabatic expansion, can lower the system's temperature without relying on a colder medium. Nevertheless, the third law of thermodynamics implies that no physical process can reach absolute zero in a finite number of steps. As a system nears this limit, further reductions in temperature become increasingly difficult, regardless of the cooling method used. In the 21st century, scientists have achieved temperatures below 100 picokelvin (pK). At low temperatures, matter displays exotic quantum phenomena such as superconductivity, superfluidity, and Bose–Einstein condensation.
Addendum 2: Rapture
The Bloom
The Song
Ecstasy
Exultation
Ubiquity
Omnilarity
Everywhere
Everywhen
Quantum Foam
Everything that can exist, does exist here. Everything that cannot exist, exists here. Everything that was and was not, what will be and will not be, exists here. This is all things, all times, all places, all thoughts, all possibilities and impossibilities.
This is the first moment, before any rules have been established, before up is up and down is down.
Ohmadrundi (a subset of machine elves) serve The Bloom.
IMAGE MISSING
Absolute Hot (Planck Temperature)
[[What Is The Hottest Temperature in The Known Universe, And Could We Achieve It]]
https://www.straightdope.com/21341968/what-is-the-opposite-of-absolute-zero
There is a limit, sort of, but it’s so inconceivably large that nobody but high energy physicists talks about it (although as I think about it absolute zero doesn’t exactly qualify as breakfast table chatter either). The highest possible temperature, called the Planck temperature, is equal to 1032 degrees Kelvin. For comparison, the center of the sun bubbles along at 15 million K (15 x 106); silicon can be created by fusion at 1 billion K (109). In short, the Planck temperature is very toasty indeed.
Some scientists believe that we, or at least our universe, have already experienced the Planck temperature, although it went by so quickly you may have missed it. It occurred at 10 -43 of a second after the Big Bang, the great cataclysm in which the universe was born. (10 -43 of a second, in case you’re not hip to the notation, is an incredibly tiny fraction of time. Time enough to create the universe, but not, as a University of Chicago physicist was once at pains to explain, time enough to get off a disputed last-tenth-of-a-second shot against the Chicago Bulls.)
Absolute zero is easier to understand than the Planck temperature. What we perceive as heat is a function of motion. The colder something gets, the less internal motion or vibration its molecules exhibit. At absolute zero — that is, zero Kelvin or -460° Fahrenheit — molecular motion virtually stops. At that point whatever the molecules are a part of is as cold as it’s going to get.
There’s a lot more latitude in the opposite direction. The faster molecules move, the hotter they get. At 1010 K electrons approach the speed of light, but they also become more massive, so their temperature can continue to rise. At 1032 K such staggering densities obtain that greater temperature would cause each particle of matter to become its own black hole, and the usual understanding of space and time would collapse. Ergo, the Planck temperature is as hot as things can get. Or at least it’s the highest temp conceivable in present theory. There’s a chance when a quantum theory of gravity is worked out we may find even higher temperatures are possible. The prospect, frankly, leaves me cold.
Addendum 3: The Mirror Realm
Also called “Ouroboros”
Chirality is not a word you are likely to hear in every day conversation, but it is at the heart of the final place we must consider: The Mirror Realm.
To understand the idea simply, look at your hands. Despite the fact that they seem functionally identical at first glance, there is no direction or method by which your left hand could be held or manipulated into being your right hand.
This feature of our reality is called “chirality” – there are structures that cannot be reshaped into their mirror images without destroying them or fundamentally changing their function.
This “handedness” goes deeper than our hands and into our DNA, the food we eat, the forces and fields that bind our base elements together and allow us to exist as complex, thinking biological systems and further extends into the other places written above.
There is a preferred direction in which we all twist that cannot be undone. Our multiverse is incompatible with the idea. To whit, “mirror” proteins cannot nourish us and “mirror” energies would be vastly different in how they functioned and may not function at all.
And yet, we see into a world that flips the direction effortlessly every time we see our own reflection in a mirror.
Mirrors offer us a window into another reality which resembles ours but where the rules are very different. As I said, we can easily project an image of ourselves into this version of reality, but could we truly step into it?
Before answering that, let us discuss the art of scrying, divining by looking into something akin to a black mirror or, rather, looking beneath the surface of the black mirror. Why would scrying produce tangible results? Why would peering into a reflection of our own world provide any insight into our own?
I have already mentioned that the laws are different in that place, but you must also consider how freely we reflect. Every drop of water and snowflake, every pane of glass, every polished boot, every silver earring, every chrome pipe, every phone screen and television, every set of mirrors attached to automobiles, produce reflections. Our entire world is reflected into this mirror realm. It is impossible to not reflect ourselves multiple time a day.
To scry is to peer sideways into the mirror realm and find insight. It is too look beyond your own reflection, to ignore it and see what lies behind it and beneath it. The scryer finds our own reality broken into pieces, fragmented, seen from a thousand different angles, atomized and rarefied down to essentials. The wise mind understands how to combine these snippets into a clearer picture of the whole than if they had seen it firsthand. This direction, seeing the back of reality, the mirror, gives them insight which can be translated back into truths valid in our own reality.
If such power can be had by simply looking how much greater would it be to walk within?
As I have said, chirality means the essence of our reality is not compatible with the mirror realm. There is life there, of a kind, but not life we would recognize. Monstrous life that only moves when we aren’t looking because our perception of it from our side of the glass renders it invisible and freezes it in time. Stare at a mirror in the dark long enough and you will start to see evidence of them in the way your own reflection morphs into something unrecognizable. But they cannot hurt us and we cannot harm them. We are simply incompatible.
However, if someone were step through the mirror, into the mirror realm itself, then we become briefly tethered to their reality. For a short time, we can breathe the air, we can walk along the surfaces, we can hear and see. All the while, our flesh is fighting an invisible battle against molecules that are not designed for us. A buzzing in the ears, a bloody nose, blurry vision, hallucinations, nausea.
And the things that live there are slowly but surely no longer bound by our perception. They turn their multifaceted eye stalks and twitch with unexpected motion, able to watch and plan.
How do you think an intelligent creature would feel about finally being able to confront one of those hateful things whose very gaze once paralyzed them?
Mirror Walkers claim that time does not pass for them on the other side of the glass. They will tell you that they cross incalculable distances in fractions of a second and that there is no living thing on the other side that can catch them because of the speed with which they traverse the place.
It is up to you whether or not you wish to believe them.
Addendum 4: The In Between
The In Between is a strange corollary to The Mirror Realm, a place visited by few and often whispered of as if little more than a fairy tale.
In stories, it is a stale, stagnant place outside of time yet between spaces. One could stay here forever and never age a day. The only cost being ambition and drive.
At the edges, a visitor can see out but cannot be seen, making it an ideal method of clandestine information gathering.
Why would this place be considered a sibling to The Mirror Realm?
The most common way to enter The In Between is to step inside a wall.
Addendum 5: The Fae
They exist. They flit between layers of reality as easily as turning a page in a book. But where are they from? Where do they live?
I can only speculate. Even the shadows merely cough and gasp in what passes for their laughter when I ask, refusing to give an answer.
Perhaps the answer lies in other liminal, transitional places such as The Fugue or The In Between. Perhaps the answer is in yet another nameless direction in which I will have to learn to peer. That would at least explain why they are so unpredictable: they operate under a different set of rules, entirely.
#Psychomancer
#Writer #Writing #Writers #WritingCommunity #WritersOfMastodon #ShortFiction #ParanormalFiction
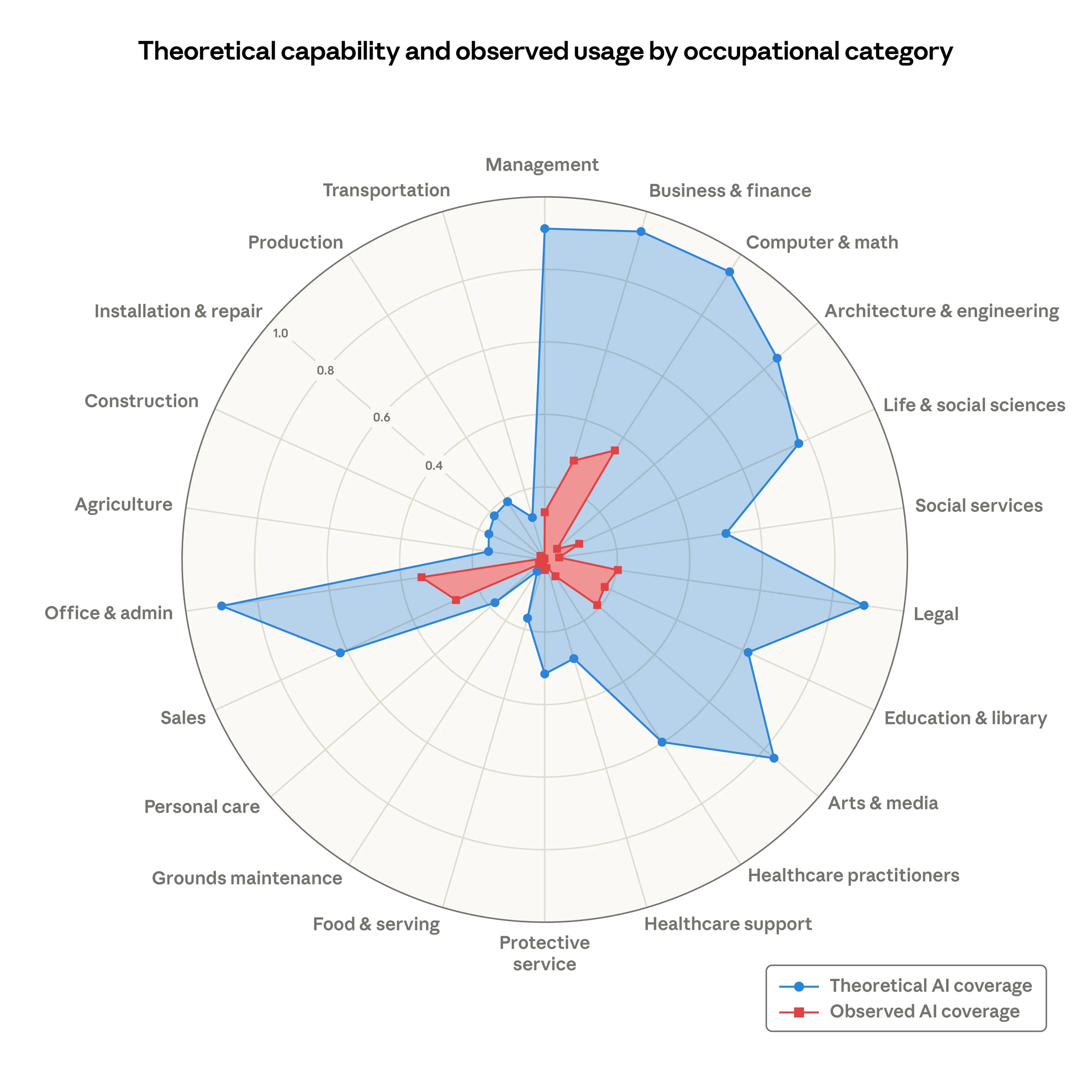
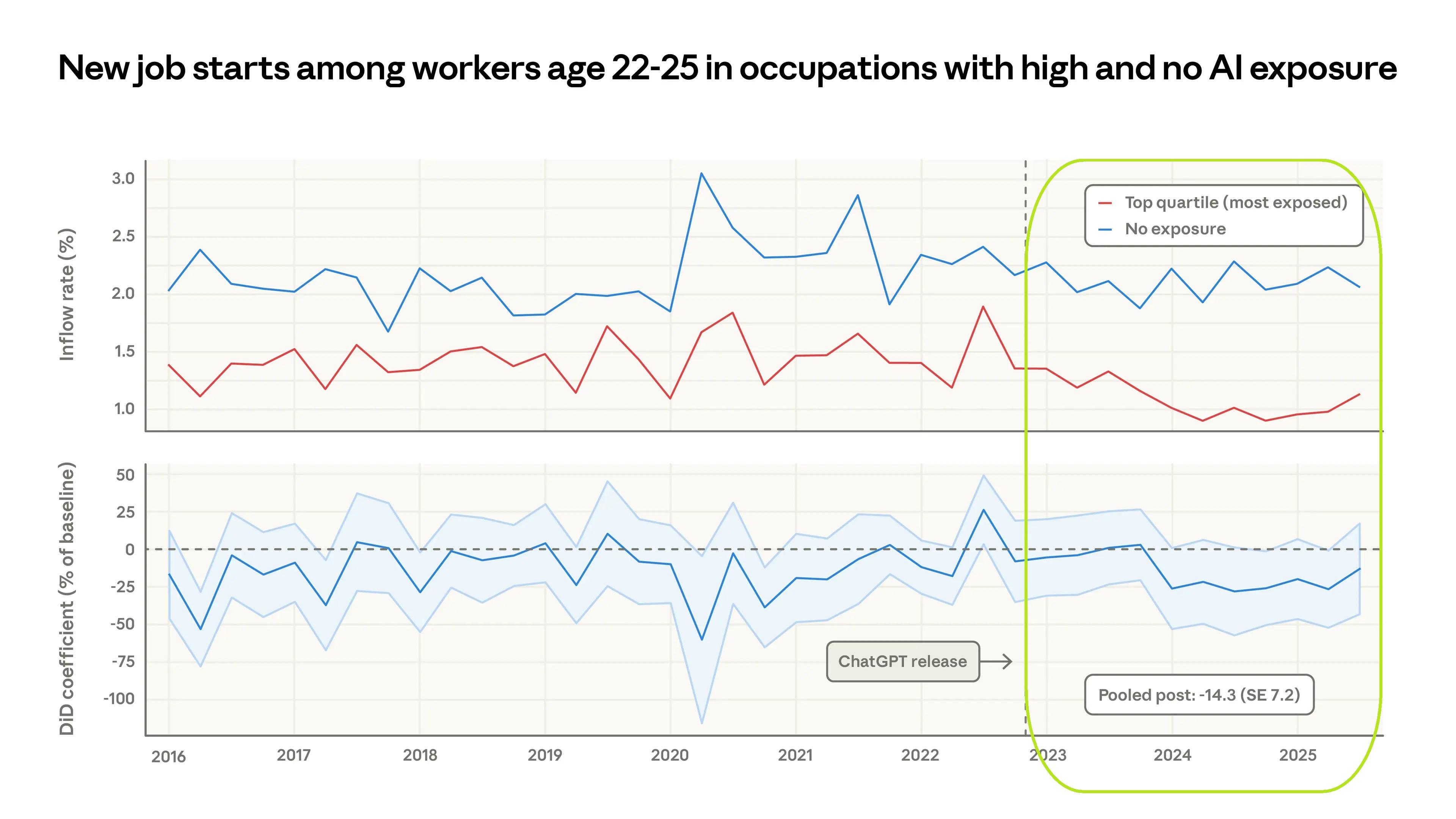 紅線為22至25歲,在AI 涉入程度高的職業的「就業媒合率」,藍線則是不受AI影響的職業的媒合率。
紅線為22至25歲,在AI 涉入程度高的職業的「就業媒合率」,藍線則是不受AI影響的職業的媒合率。










