By the Lake
I read everything at the info kiosk of the Lake Ochonkmah Otter Lodge.
It used to be a hunting shack for otter hunters but was abandoned sometime around 1900.
In 1943, a husband and wife research team, Drs. Bartholomew and Candice Burroughs “rediscovered” the location while hiking around the lake and studying the local otters, which were rumored to be particularly sociable and friendly. They made camp on the site and made note of its location. Over multiple trips it became a bonafide research station and was repaired, built-upon, and expanded.
It was their life's work for 30 years and they developed a niche following among otter aficionados. The otters at Lake Ochonkmah were very friendly and completely unafraid of humans. The Burroughs speculated that the hunting had been easy and they never had a good explanation for it being abandoned.
One theory, borne out by examining remains, was that a mystery illness had thinned out the otters and wiped out the humans who knew about the location, leaving it free to recover and flourish.
The only reason to visit this place was to watch the otters. The water was far too cold year round to be comfortable for swimming and there were precious little in the way of game fish left after the otters had their fill.
Still, a small town grew up during the height of the Burroughs' research, a country store for supplies and a bed and breakfast style boarding house for transients and travelers.
On October 15, 1975, Candice died in her sleep at the age of 61. There was no warning as she had been working with Bart the day before and gave no indication of being sick. Bart became understandably withdrawn and depressed and focused on his work. Less than a month later, he died in his sleep, as well, on November 22, 1975. He was 63.
Without the support of the doctors, the research station fell into disrepair and what little tourism there had been stopped entirely.
In 1987, the millionaire Margo Fillings swept in like a tornado and revitalized everything.
She never said why she was so passionate about this place, but she turned the old research station into an overnight learning experience and encouraged schools to bus kids in to learn all about the Ochonkmah Otters.
The general store was re-opened with a more worldly selection of goods, snacks, candy, soda, and the like.
The bed and breakfast was remodeled into a proper family restaurant with the rooms being used to house the staff.
A motel opened just outside of town to accommodate any other travelers.
The rest of my class was still in the observation room where it was kept dark so you could peer out the long glass floor to see the otters in their natural habitat.
I was out in the well-lit hallway, trying to talk to the guide, but she kept ignoring me, telling me she had somewhere she had to be and going back and forth between an office in the back and checking on the observation room.
She ran back and forth and back and forth.
She had to squint to see inside the observation room and she'd look inside and shake her head.
And then scurry back to the office.
I didn't want to go into the observation room so I stayed out in the big lobby and read the infographics again.
Margo Fillings was the savior of the town according to the infographics.
She looked like a gymnast in her photos: short build, athletic, with thick legs, an attempt at a pixie cut but her red hair was too curly to stay down. Always smiling. Always looking directly at the camera.
My legs were thick, too, but so was the rest of me. Not so athletic.
Sometimes, my legs would stop working and I'd have to sit down or lie down, but that didn't happen very often.
When the other kids from my class started to filter out of the observation room, I was looking for Angela and Angie, the best friends I'd ridden down with.
Angela was really smart, good at math like I was, but also good at music which I wasn't. Angie was an artist and barely passed any other classes, not because she couldn't but because she didn't feel like it was worth the effort.
They were my friends, my only real friends.
I had trouble making friends because I was prone to talking too much or saying the wrong thing. I did that all the time. I said the wrong thing and people got mad, but never told me why they got mad.
Angela came out and she was rolling her eyes while walking toward me.
“Angie found a boy,” she told me.
Angie would latch onto a boy and obsess over them.
Then she would date them, get to know them, and suddenly get over them.
Angie came out with her arm wrapped tightly around a tall boy's waist.
He wasn't even handsome or pretty. He had stringy hair and his clothes were too baggy.
He looked dirty.
“He plays the fucking guitar in a band,” Angela told me.
That explained it, apparently.
Everyone else left, teachers, chaperones, students.
Everyone left except for Angela, Angie, Angie's new obsession and his “bandmates” who were just as dingy and he was.
Angie was pale and raven-haired like an angel might be, but she preferred to wear black, even her makeup was black.
Angela wore light blue slacks and a silk blouse. She was always so exquisite.
We stayed two more days, at the motel outside of town.
On the third morning, Angie was gone.
Angela told me that she'd left with the band and we'd be lucky to see her at all for a few weeks.
She was 17 and she liked to pretend she was an adult.
Angela was really quiet that day.
I think Angie didn't tell her that she was leaving with the band.
When I woke up the next morning, Angela was gone. Her clothes, her toiletries, her bag, and her car were all gone.
I walked back to town and into the Otter Lodge.
I walked in and told the lady who worked there, the same one from the overnight visit, that I was lost.
She asked me my phone number and I didn't know.
She asked me for my parent's names and I didn't know.
She asked me for my name and I didn't know.
According to Margo Fillings, the anomaly was here on her first visit to the town, back when she was first considering pouring her resources into it.
It looked like a teenaged white girl. Limp brown hair, a little pudgy, a little slow witted, but it spoke like a normal teenaged girl and it was wearing normal clothes.
She thought it was a mannequin because it was motionless, not breathing or moving. Its eyes were wide open, not blinking.
She touched it.
The skin was warm to the touch but stiff.
It shivered at her touch and immediately became supple.
Its chest began to rise and fall. When she looked at the face again, the eyes had closed. It appeared to be sleeping.
She assumed it was a runway and woke it up.
It's first words were, "Hi, Margo!"
Margo says she maintained her composure, but "citation needed" you know.
When she asked it "What's your name?"
It replied something like, "Don't be silly; you know who I am."
So she gave it a name, "Lillian", after the flower, and it took it.
We know this because Margo kept a journal. I've read it. It's practically Exhibit A.
The journal says "I said the first name I could think of. I remembered seeing lilies out front, so I called her Lillian. It was a question, I asked her if her name was Lillian and she agreed that it was. That wasn't what I was asking, but she just accepted it."
But if you ask Margo about it now, she will tell you that the anomaly is, in fact, "Lillian Harper" and that she was always "Lillian Harper" and that they knew each other before she found her in the back of the research building gathering dust, before she gave her a name.
One time, a guest was here with her fiancé.
She was so kind, wearing white to contrast her dark wavey hair. She spoke like a poet, it was mesmerizing. She wrote about the trees and the flowers and the lake and the otters.
She found beauty everywhere she looked. Decaying leaves, moss, and mushrooms covering a fallen tree trunk. An otter's corpse washed up on the shoreline. The sun on her face and in her eyes. Storm clouds flashing in the distance. The sounds of the wind blowing the ghost lights over the water at night.
Her fiancé was comparatively grumpy. He was a writer, too and they thought this place would inspire them both.
For him, it was uncomfortable, aggravating his allergies, covering him in ants and spiders, spoiling their food. He only saw unnecessary turmoil.
There can be beauty in unexpected difficulties, right?
She saw it. Her eyes sparkled with it; her soul glowed and reveled in it.
She was kind to me, even though I couldn't walk.
I was in a chair most of the time. I would be in my spot in the chair outside the old research center in the morning and back in my room at night.
My arms worked, my lungs worked. I could breath and speak and think and smile.
But my legs felt like nothing at all. Like empty shells filled with dirt.
Like anchor weights tied to my pelvis.
I told them stories about the otters and about the people who used to work and live here.
I told them about the Drs. Burroughs and how they both died but nobody knew why. I thought it was the sadness.
This place had a sadness about it, always, but people would come and cover it up and ignore it.
They would find the life, the singing of the insects, the splashing of the otters, the waving of the trees, and ignore the emptiness underneath it.
They would study and sleep and observe and feel and love and eventually it would find them.
They would wonder where it all went and why it took so long to notice it was gone.
“Melancholy” they called it.
She thrived and grew and blossomed.
He withered.
All he left behind was a perfect bouquet of white lilies.
She threw them on the ground right in front of me.
They didn't wither.
They flourished.
They've had to send multiple agents because every other agent eventually believes the lies.
First question I asked? "Why not take it to a real lab instead of doing all the study here at a compromised location?"
Answer: Any attempt to remove the anomaly from the site results in tremors that get worse the further away it's taken.
So they keep sending us and once we stop sending in updates, they come and get us and send in someone else.
I've seen the photos and the records of the examinations of the anomaly and it definitely is not human.
It has the outward appearance of a teenage girl, but only superficially.
It's anatomy has been thoroughly detailed while it was in its dormant state.
Constant body temperature of 96° regardless of the outside conditions.
Smooth skin resembling that of a typical Caucasian but only from a distance. There are no pores and no body hair, not a single blemish. The skin cannot be cut or punctured using any methods we've devised and it doesn't bruise. There is no evidence of veins or blood flow of any kind, no pulse at all.
It has the shape of breasts but no nipples. It has buttocks but no anus. Instead of a vaginal canal and urethra, it has a shriveled phallus with no openings. There are no visible testes.
The head appears almost entirely human. It has nostrils that seem to lead to a nasal cavity. Eyes with tear ducts that react as expected to light even when it is dormant. It has eardrums and eye lashes and eye brows. All the hair on the head seems to be attached as expected even when the rest of the body has none at all. It has a mouth with the correct looking teeth, a tongue, a trachea and esophagus, but its internal structure remains a mystery.
Endoscopy hits impossible dead ends when run down either throat tube.
It doesn't breath when it's dormant so we aren't even sure if it needs air.
While dormant, it has been submerged in water for prolonged periods without any ill effects.
We have observed that when it returns to its active state, sometimes only parts of the body revive fully, such that it appears to be paraplegic or quadriplegic. It compensates by entering a semi-dormant state and "floating" between locations. Even when done in full view of locals, none of them recall seeing it happen.
It has never demonstrated this ability while fully active, only while semi-dormant, a state that resembles "sleeping".
One time, my friends put on a musical production of Grease.
They know that I love musicals and singing even if I can't participate.
They staged it around the Lodge so I could sit out front. Even though I couldn't walk and had trouble speaking, they made sure I felt like part of the show.
I was able to move my arms and smile to “You're the one that I want!”
“Oh yes, indeed!”
The spectators noticed and the cast sang “We go together” to me while I was able to shift back and forth.
It elevated everybody's spirits.
After the musical was over, after the people had said their goodnights to each other and to me.
After I basked in the feeling of accomplishment and acceptance, I drifted off to sleep.
I dreamed of swimming in the lake. The water is far too cold for swimming in real life, but it was warm in the dream.
I was so far out that I couldn't see the shore on either side. The lake isn't that big, but in the dream it was.
I wasn't afraid. I wasn't afraid at all because the water was calm and it supported me.
Deep, deep below me, I could see lights and motion as if an entire city were down there.
I wanted to go down there. I wanted to see who it was.
But my head refused to go under the water. I would try but the water would push me back.
The water wanted me to stay up here.
I could almost hear them building something, creating something marvelous.
But it wasn't for me.
We've checked air, water, food toxicology. We've bagged insects and plants for allergens, poisons, or venoms.
We've run up antenna to check for electromagnetic sources, Geiger counters for radiation, specialized microphones for ULF, ELF, UHF, and EHF.
Nothing.
We've even had Astrologers, Diviners, and Ley Line experts check it out.
The local Native Americans were, unfortunately, driven out and killed by settlers long ago. The only record we have is the name of the lake itself, "Ochonkmah", which looks like it's derived from something Native American but is too bastardized for a direct translation. It resembles the Choctaw word *achukma* which has positive connotations of "good" or "pleasing".
The only other anomaly is a strong magnetic source out in deeper waters, assumed to be an ancient meteorite. It's far too cold and deep for regular divers and we've yet to get permission to field a top-of-the-line manned submersible or ROV. Camera and robot claws we drop on lines inevitably hit snags. Cameras show significant debris around the site. What artifacts we've hauled up matches what we would expect from Viking long boats. There is no good reason to find that sort of debris at this location.
The magnetic source could help explain the ghost lights which are known to float over the water during particularly warm autumns.
We've caught them on film multiple times with various cameras. The purple glowing globules read very similar to St. Elmo's Fire. They cannot be ignus fatuus due to the lack of flammable gas. We've yet to have a boat on the water fast enough to observe them up close.
It had to be a dream, but it felt so real. It had to be a dream since nobody else saw it.
There was a festival in the main yard, but I was on the shore looking out over the lake.
I saw a silvery disk come out of the sky and make as if to land on the surface.
Before I could think, I was in the water, swimming with all my might toward it.
The water is too cold to swim in, but I was swimming and it wasn't that cold.
I never swam so fast before. My legs worked better than they ever had and pushed me forward while my arms carved great handfuls of water over and behind me, like I was climbing a mountain of snow.
I reached the disk and it was tiny, no bigger than a Frisbee.
I was certain it had been a spaceship but here it was no more than a toy.
I stopped swimming and found I could stand. The water out here should be quite deep but I stood up.
I looked back toward the shore and saw a tall, purple skinned humanoid motioning for me to pick up the disk.
His skin was dark and smooth, leading to thin arms that moved more like tentacles than something with bones and joints. His head was round like a matchhead and his eyes were black.
His slit-like mouth was smiling.
I'm not sure how I could tell it was smiling, but it was.
I picked up the disk and he pointed out further into the water.
I turned and saw a massive blobby creature, like something made of the squishy from the bottom of the lake.
It was rushing away from us with a massive crooked wake.
Parts of it seemed like stones or rocks and two of them turned and I saw they were huge eyes, watching my hand holding the disk.
I held it close to my chest and flung it out like a Frisbee and the blob leaped after it, a giant mass of barely held together pieces shaped into a huge dog's head on a turtle's body with flippers for legs.
It grabbed the disk in its mouth and collapsed back onto the surface of the water with a SLAP.
The purple creature was applauding me and motioned for me to come closer.
Occasionally, this place hits the news cycles and tourism has a temporary boost.
The businesses open back up, people show up to run them. People show up and buy tickets, souvenirs.
The otters get to entertain a new batch of people.
It goes like it always goes here.
It's great at first, then it gets rougher, then it gets angrier, then something bad happens and it dries up.
Disappearances usually.
Maybe murder but no bodies are ever found.
Rumors start to flow.
People get afraid again.
It goes dormant.
The anomaly is always part of the revival and she reacts very poorly to the negative happenings.
She plays really hard at being upset and not understanding why people can't be kind and get along.
There is no way to know if it is "genuine" sadness as she isn't human to begin with.
She's very convincing and seems to know intimate details of the lives of those who live here. She can speak to their wants, needs, dreams, fears, weaknesses, everything as if she is their best friend in the whole world.
She knows things about me that I won't put down in a report.
She knows things about our research that she shouldn't. When she gets deep into esoterica, her voice changes a bit, becomes monotone, almost like she's reading a script.
Ask her about it afterwards? She claims she doesn't remember and seems to freak out if you play back a recording of it.
I'm not sure how we can keep things from her as she seems to know everything that happens around the lake, including internal thoughts that are never voiced or written at all.
It may be too dangerous to continue the investigation and we may want to write off our losses and leave it be.
I thought I was like a daughter to her.
She took me in and I lived and slept under the same roof as Imelda, Margaret, Stephanie, and Beatrice.
I was there for their first loves and their first heartbreaks.
I was there when they wondered what the point of it all was.
I helped them find meaning. I helped them understand the nature of people and of men.
I thought they would be strong enough to go out on their own, but they always went back to someone.
They seemed to not know themselves unless they were supporting a man.
It was sad and I told Mrs. Glenn it was sad and she agreed with me.
Mrs. Glenn and I wanted the girls to be self-sufficient like she was.
She raised all four girls without a man and she did a fine job.
Being the proprietor of the restaurant meant she had room and board for them as long as they worked.
She never did put me to work on the floor and she never told me why not. I asked and asked until eventually I stopped asking.
But I helped her with my stories and with my advice.
I told her about the history of the lake and the research station and the fur trackers and the otters.
I told her about the ghost lights and about the silver disk that came down from the sky.
I told her about the riches that had been lost time and again by strange ships that should never have tried to sail.
I told her about the plants and insects and which ones were safe and which ones were to be avoided.
She spun those into the recipes a little at a time, spreading good cheer and health with each meal sold.
When Imelda left, no note, just all her things gone and her and her boyfriend nowhere to be found, she came to me and I had no answers.
Imelda hadn't confided in me. None of the girls confided in me anymore.
When I asked them why, they told me they “outgrew” me and that was that.
But Imelda had been distant for a long time, keeping to herself.
Margaret was learning how to cook the special recipes with her mom and Mrs. Glenn couldn't be happier.
It made no sense for her to be the next to leave without a word.
But she was gone. Her clothes were gone. Her man was gone.
Imelda had never called and she expected the same from Margaret.
She didn't asked me for advice this time.
She didn't talk to me for a long time.
Not until Stephanie was the next to go missing.
She talked to me “before Beatrice went away,” she said.
She told me she knew what was happening and she thought she was paying her dues.
She thought she was doing what was required by making the recipes and serving them.
She said her missing girls sang dirges to her from the deep water.
They sang to her and told her that she failed them and failed everyone and that the lake would take its price one way or another.
She told me all this like I could do something about it, like I was part of it.
I didn't understand, but I asked her what she thought the price might be and if she thought it was worth it, if she thought she might be willing to pay it if she knew what it really was.
I asked her that question because I wanted her to figure it out on her own. I wanted her to think about what was important to her. I wanted her to recognize the love she had for her daughters and how that was clouding her judgement.
I didn't know what she would do.
She drowned herself in the lake.
Beatrice took over the restaurant.
I was sent back to the research station.
She never talked to me again.
The otters here are another part of the anomaly. They are obsessed with humans. They study us just as much as we study them. They've formed a particularly large raft and maintained it over generations, which is quite unusual. The males and females and the offspring all seem to stay close. There are so many of them that, even though the lake is very large, there are very few game fish left for anglers to catch.
Some say they should have run out of food by now, but they obviously haven't.
They don't seem to be any smarter than other otters, but they ratchet up the curiosity.
So when they suddenly pulled away from the shore where the settlement was located, it was odd.
They were acting strange. The locals didn't seem to care much, even though much of the tourism relied on them.
It was doubly unfortunate because Lake Ochonkmah and the Otter Lodge had been featured on some popular podcast which got it recognized by real celebrities who were stopping by for photo ops.
I think after Tiger's birthday party, though, that the tourism will die back down, due to all the bodies they found.
The only one who noticed or cared about the otters was Melanie.
She definitely noticed during the birthday party and tried to get Mr. Fletch, who runs the tours, to do something, but he wasn't there.
Once he got back, I think she sent Axl Fucking Rose up there to talk to him. I was close enough to hear Mr. Fletch yell at him, telling him to mind his business and that he didn't care if they were sick as long as they were still in the water.
When I left the lodge, I noticed a white and red helicopter in the yard that had not been there before. Further away, toward the road I saw an area cleared of trees and a small, personal airplane was parked, also white and red. Toward the lake was a white and red jet ski. I noticed they all had little red ribbons on them and thought they must be presents.
A group of people were walking in from the road, surrounding an attractive black man in white slacks.
I recognized him: Tiger Woods.
I was excited that our little outpost was so famous that someone like him would visit and I realized it must be a birthday party.
I went down to the water to stay out of the way.
I wanted to see if the otters had returned to this side of the cove.
Once I scrambled down and got a better look, I saw that they were still as far away as they could be without going out into deeper water.
Additionally, they seemed to be agitated and moved in jagged bursts in the water.
I climbed back up the embankment and went to the General Store where Mr. Fletch ran the tours.
The small desk and register were vacant. I looked at the books and post cards and the souvenirs and smiled.
A man with long red hair came in and asked me a question.
“Excuse me, but is there something wrong with the otters?”
I was so excited that someone else noticed.
“I was thinking the same thing,” I said.
“I know the local bevy has a reputation for being friendly, but even for normal otters, they seem distressed.”
He explained that he noticed their fur was matted which would terribly diminish their ability to keep warm and swim.
I explained that they were normally on the near shore and that they'd fled to the other side days ago, long before everybody else showed up.
I further told him that I wasn't able to get any of the adults to understand how grave the situation was, not even the docents at the Lodge.
He was puzzled but didn't have anything else to say.
The party was starting and I went back down to the water's edge.
I saw the nice man with red hair go back to Mr. Fletch but Mr. Fletch seemed to be angry about something so the nice man left again.
I was so worried about the otters that I decided to go to them.
I slipped into the freezing water, not shivering, but feeling my legs go numb almost immediately.
I pushed deeper and started swimming.
I wasn't fast like I'd been in my dreams.
I kept my head above the water because I knew that would be the end.
I swam toward the otters and they ignored me.
I swam and felt something touch my legs.
I treaded water and looked down.
I looked down and the water was super clear.
It was clear and I saw Angie down there.
I saw Angie, I saw Dr. Candice Burroughs.
I saw Angie, and Dr. Candice Burroughs, and Margo Fillings, and Camilla Harper the poet.
I saw Vanessa Glenn and her daughters Imelda, Margaret, Stephanie, and Beatrice.
I saw them reaching for me, their smiling faces and their long outstretched arms and fingers.
I felt them touching my feet and my legs.
I expected them to be angry, but they were at peace.
They wanted me to be at peace.
I thought about how I was never truly loved here.
Nobody accepted me.
Nobody understood me.
I was merely tolerated.
I was never part of a family.
I was never a friend, only an acquaintance.
I didn't belong here.
I never belonged here.
I belonged somewhere else.
I belonged somewhere else.
Instead of going under to where they were, I floated on the water until it was golden.
Until the sky was silver and the water was gold.
I floated and I saw a place of crystal and glass, glowing with internal light.
I saw them standing on the platform embracing and laughing.
All the woman from the water were up there and they were happy.
I floated toward them.
I wanted to join them, but the platform was too high and I wasn't allowed.
I wasn't welcome.
I sank away and wanted to cry.
I wanted to be alone and to cry.
A strange woman approached me.
Her face was plastic and her hair wasn't real.
She approached me and said, “I am your mother.”
I never had a mother before.
I heard her say “I am your mother” and the voice was pure bliss, like melted chocolate and rainbows and warm nights and the kiss of a kitten's whiskers.
I heard her and I believed her.
I believed her and I let her embrace me.
Like I said, a dozen bodies from the lake, all perfectly preserved, all women who went missing, even a couple nobody knew were missing yet.
A dozen bodies found on one hand and the disappearance of Melanie, the anomaly herself, on the other.
You know what the main office told me?
"Forget about it. It doesn't matter."
END_OF_LINE
#WhenIDream #Dreams #Dreaming #Dreamlands #Writer #Writing #Writers #WritingCommunity #ShortFiction #Fiction #Paranormal
CC BY-NC-SA 4.0
This work is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License
Mastodon




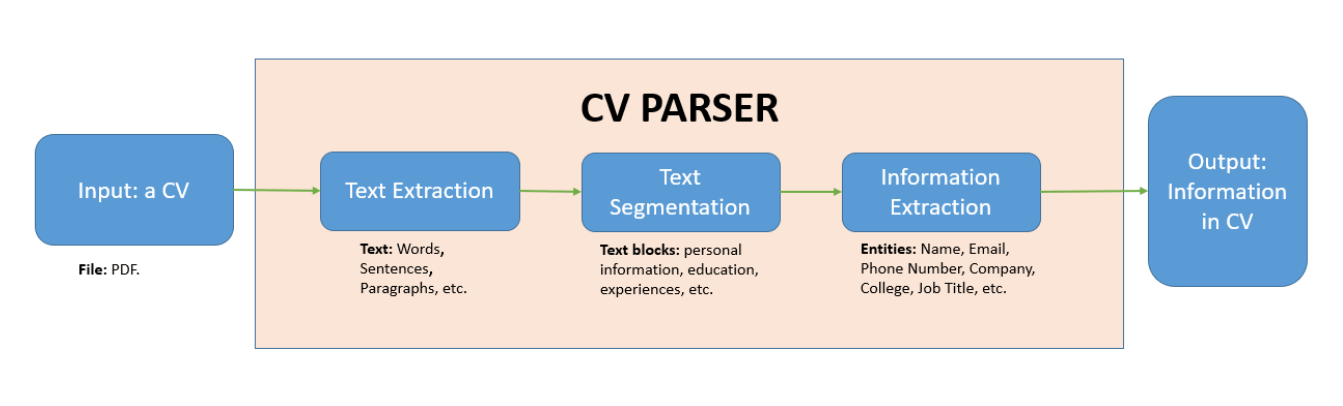 Image: a typical resume content extraction workflow from neurond.com
Image: a typical resume content extraction workflow from neurond.com

 O historiador grego do século I a.C., Diodoro, é considerado um compilador de fontes antigas, dentre elas alguns dos ensinamentos de Demócrito de Abdera. Em sua obra, Biblioteca de História (Tomo I, Capítulo 8), encontramos um relato da origem dos seres vivos e dos primeiros homens, que são atribuídos aos ensinamentos de Demócrito por especialistas como Diels, Vlastos, Reinhardt e Beresford. Dando início a meus estudos sobre Protágoras que, como discípulo de Demócrito, compartilhava com ele algumas concepções naturalistas e humanistas, apresento uma tradução do relato da pré-história de Diodoro.
O historiador grego do século I a.C., Diodoro, é considerado um compilador de fontes antigas, dentre elas alguns dos ensinamentos de Demócrito de Abdera. Em sua obra, Biblioteca de História (Tomo I, Capítulo 8), encontramos um relato da origem dos seres vivos e dos primeiros homens, que são atribuídos aos ensinamentos de Demócrito por especialistas como Diels, Vlastos, Reinhardt e Beresford. Dando início a meus estudos sobre Protágoras que, como discípulo de Demócrito, compartilhava com ele algumas concepções naturalistas e humanistas, apresento uma tradução do relato da pré-história de Diodoro.