Para quem inicia no Mastodon aqui vão algumas explicações sobre a importância que as hashtags possuem.
 A hashtag é uma palavra ou frase que, uma vez precedida pelo símbolo de cerquilha (#), sem espaços, transforma-se em uma etiqueta ou rótulo, na forma de um hiperlink que leva para uma página com outras publicações relacionadas ao mesmo tema.
A hashtag é uma palavra ou frase que, uma vez precedida pelo símbolo de cerquilha (#), sem espaços, transforma-se em uma etiqueta ou rótulo, na forma de um hiperlink que leva para uma página com outras publicações relacionadas ao mesmo tema.
No Mastodon, bem como em toda federação ActivityPub, a compreensão de suas funcionalidades é essencial, inclusive por questões de acessibilidade.
Barra de pesquisa do Mastodon
Por motivos técnicos de privacidade o Mastodon foi inicialmente desenhado para permitir apenas as seguintes formas de busca:
- Por hashtags (#exemplo);
- Pessoas (@nomedousuário@domínio);
- URL (links) de perfis e de posts;
Atualmente o mastodon permite a busca por texto simples, mas para que as postagens dos usuários se tornem visíveis é necessário que optem por isso (então se você quer que o texto de suas postagens públicas sejam vistos na busca, acesse as configurações de sua conta e marque para permitir essa opção).
A pesquisa por hashtags é precisa e abrange todas as pessoas de instâncias federadas à sua, independentemente de você seguir a pessoa ou não, e sem a influência de qualquer algoritmo.
Note também que você pode seguir uma hashtag, caso seja um assunto do seu interesse, clicando no botão destacado acima. Quando você segue uma hashtag, todas as postagens das pessoas pertencentes à sua instância ou das instâncias federadas à sua, independentemente ou não de você segui-las, que contenham essa hashtag, serão exibidas na sua página inicial.
As hashtags, portanto, devem ter um # no início e não podem ter alguns caracteres especiais no início e no meio (ponto, espaço, arroba, asterisco, etc.).
O sistema de hashtags atualmente não diferencia a acentuação e alguns caracteres especiais que são permitidos, como o (ç), por exemplo, de modo que as hashtags #política e #politica (sem acento no i) ou #paçoca e #pacoca, são unificadas pela busca da plataforma.
Se você deseja pesquisar uma frase, digite tudo como uma palavra, como #CatsOfMastodon.
Se você deseja que sua postagem seja encontrada com mais facilidade nas pesquisas, inclua muitas hashtags relevantes. Não há problema em usar muitas dessas etiquetas, as pessoas entendem que são necessárias nesse tipo de sistema de busca.
Ademais, o uso das Hashtags devem respeitar uma relevante questão de acessibilidade. Existem muitos usuários cegos no Mastodon e no Fediverso que usam leitores de tela para converter texto em áudio.
Portanto, ao postar hashtags, existe uma formatação correta, que consiste no uso do método chamado de CamelCase (onde cada palavra começa com uma letra maiúscula), por exemplo #CatsOfMastodon em vez de #catsofmastodon. As letras maiúsculas permitem que os aplicativos de leitura de tela separem as palavras corretamente e leiam a hashtag em voz alta corretamente.
Aliás, é importante mencionar uma hashtag super relevante do universo Mastodon, a famosa #Alt4Me.
Quando uma imagem de uma postagem não possui descrição e há a hashtag #Alt4Me adicionada a ela pela pessoa que a postou, isso pode significar que o autor da postagem não consegue adicionar uma descrição (por exemplo, devido a uma deficiência), mas esteja ciente de que é necessário, então ele adicionou a etiqueta preventivamente.
A hashtag #Alt4Me geralmente significa que uma pessoa cega quer que você escreva uma descrição da imagem. Responda à postagem com a hashtag e forneça a descrição.
Note que a sistemática de hashtags não faz distinção se as palavras estão em caixa alta ou caixa baixa, portanto, #CatsOfMastodon ou #catsofmastodon são exatamente a mesma coisa para fins de pesquisa, de modo que o único diferencial em seguir o “CamelCase” está em propiciar um ambiente mais acessível às pessoas cegas, que deve ser respeitado.
Outra funcionalidade importante das hashtags é que elas permitem às pessoas que não querem ver postagens relacionadas a determinado assunto ou tema, que utilizem um filtro cuja função é tornar esses posts invisíveis, sem a necessidade de silenciar, bloquear ou deixar de seguir um usuário.
Ao utilizar o Mastodon é muito importante que você compreenda que se trata de uma rede social que recebe e acolhe pessoas que vieram de outras redes sociais, de propriedade capitalista, buscando um ambiente menos tóxico.
Sendo assim, existem temas que devem ser rotulados pelas hashtags não só para facilitar que pessoas interessadas os encontrem, mas também para permitir que pessoas que se incomodam com eles os filtrem.
Vamos usar como exemplo o caso do futebol. Eu adoro o esporte, tenho meu time de coração (Flamengo) mas convenhamos que há pessoas que não veem a menor graça e, ademais, existe uma “cultura do futebol” em nosso País, que é extremamente problemática, incluindo violência entre torcidas, machismo, homofobia e racismo.
Não custa nada, portanto, incluir a hashtag #futebol em suas postagens sobre o tema, ou outras em temas sensíveis, como #PolíticaPartidária.
Evidentemente você também tem a ferramenta dos avisos de conteúdo, mas acho a hashtag mais eficiente, pelo fato de permitir que os interessados encontrem a postagem, bem como os desinteressados a tornem completamente invisível sem sequer a necessidade de ler o aviso de conteúdo sobre o tema.
Aqui explico, portanto, como filtrar as hashtags.
No menu lateral vá em Preferências > Filtros e depois clique em Adicionar Filtro. Abrirá a seguinte tela:
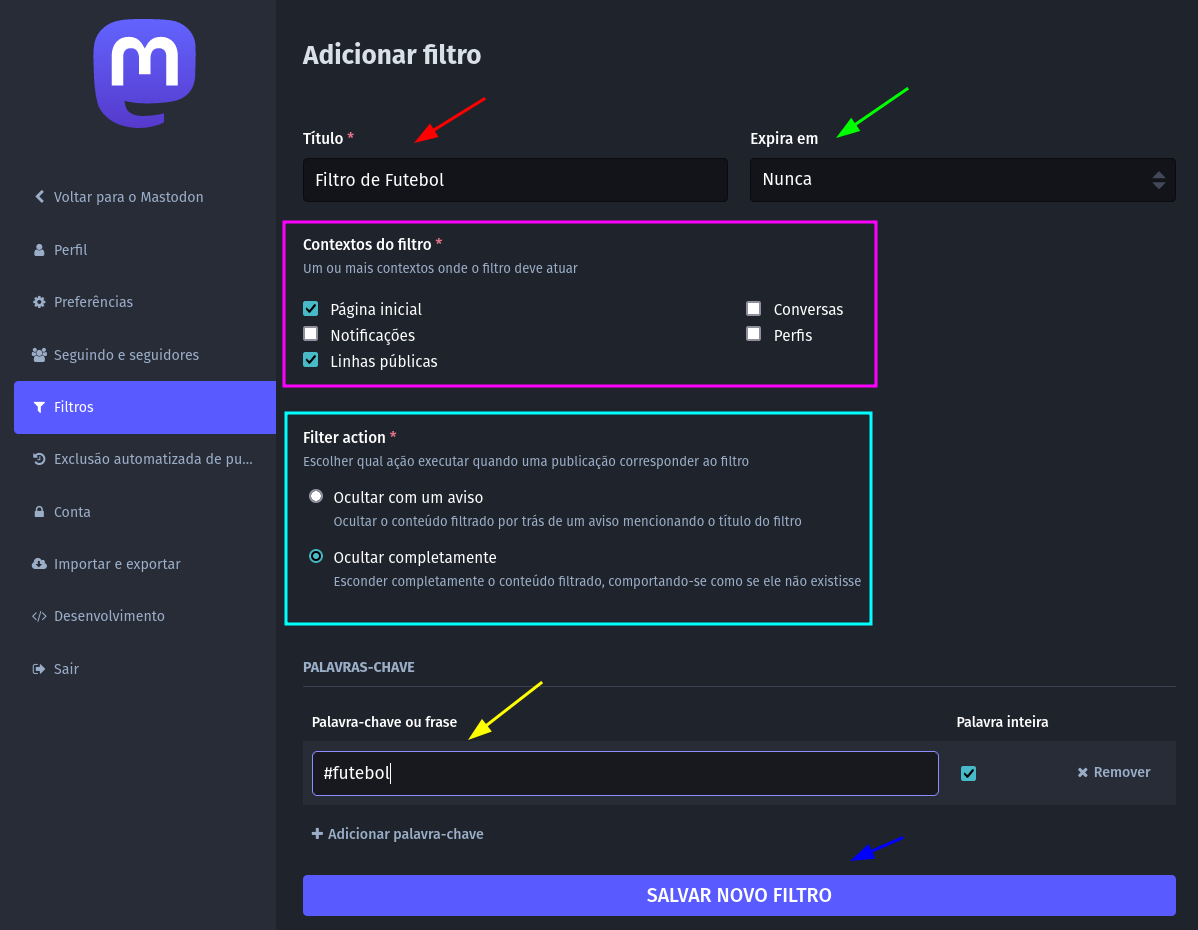
O título do filtro, indicado pela seta vermelha, como o nome diz, é apenas um título, para te ajudar a encontrar o filtro em sua lista de filtros.
A seta verde indica o tempo de validade do filtro (que pode ser permanente, como visto no exemplo). Às vezes você não se importa em visualizar algo sobre futebol ou política, mas durante os jogos ou durante o período eleitoral, você não quer ser inundado de postagens sobre o tema, de modo que pode criar um filtro com duração provisória.
Em “Contextos do filtro” (retângulo rosa) você escolhe onde o filtro vai exercer sua função de ocultar mensagens, no exemplo dado marquei a opção de ocultar as postagens da página inicial e das linhas públicas, mas você pode fazer uma filtragem mais severa, se preferir, filtrando perfis de usuário e conversas.
Em “Filter action” você pode escolher se a postagem filtrada vai ser indicada para você com um aviso ou se ela desaparecerá completamente sem qualquer notificação, como se a postagem jamais tivesse existido.
Em “Palavra-chave ou frase”, indicado pela seta amarela na parte de baixo, você digita a hashtag que quer filtrar.
Após Salvar Novo Filtro, conforme o botão indicado pela seta azul, você não irá visualizar qualquer postagem em sua linha do tempo ou nas linhas públicas que contenham a hashtag selecionada (no caso do nosso exemplo: #futebol).
Você pode adicionar quantos filtros desejar.
Essas eram as minhas considerações a respeito das hashtags. Espero que aproveitem bastante e criem muitas hashtags interessantes no universo brasileiro do Mastodon.
#Hashtag #MastoDicas #Mastodon #Tutorial

 A hashtag é uma palavra ou frase que, uma vez precedida pelo símbolo de cerquilha (#), sem espaços, transforma-se em uma etiqueta ou rótulo, na forma de um hiperlink que leva para uma página com outras publicações relacionadas ao mesmo tema.
A hashtag é uma palavra ou frase que, uma vez precedida pelo símbolo de cerquilha (#), sem espaços, transforma-se em uma etiqueta ou rótulo, na forma de um hiperlink que leva para uma página com outras publicações relacionadas ao mesmo tema.