from Stories of Salt
aaaaaaa
Read the latest posts from Infosec Press.
from Stories of Salt
aaaaaaa
from 📰wrzlbrmpft's cyberlights💥
A weekly shortlist of cyber security highlights. The short summaries are AI generated! If something is wrong, please let me know!
💰 Krypto-Betrüger: Sechs Österreicher festgenommen cybercrime – Six Austrians were arrested for running an online scam involving a supposed new cryptocurrency, defrauding investors of millions. Europol coordinated the operation, seizing over 500,000 euros in cryptocurrencies, 250,000 euros in fiat, and other assets. The suspects falsely claimed to open an online trading company with a new cryptocurrency, carrying out an Initial Coin Offering (ICO) without transparency, leading investors to realize they were deceived in February 2018. https://www.heise.de/news/Krypto-Betrueger-Sechs-Oesterreicher-festgenommen-9714300.html
Lockbit Corner 🛑 Law enforcement seized Lockbit group's website again cybercrime – Law enforcement seizes Lockbit group's website, threatens to reveal identities. https://securityaffairs.com/162778/cyber-crime/law-enforcement-seized-lockbit-site-again.html
⛓️ U.S. Charges Russian Man as Boss of LockBit Ransomware Group – Krebs on Security cybercrime – U.S. charges Russian man as boss of LockBit ransomware group, part of elaborate criminal network. https://krebsonsecurity.com/2024/05/u-s-charges-russian-man-as-boss-of-lockbit-ransomware-group/
🎙️ In interview, LockbitSupp says authorities outed the wrong guy cybercrime – LockBit leader denies being correctly identified. https://therecord.media/lockbitsupp-interview-ransomware-cybercrime-lockbit
🍧 LockBit gang claimed responsibility for the attack on City of Wichita cybercrime – The City of Wichita was hit by a LockBit ransomware attack, leading to network shutdown. The LockBit gang threatened to leak stolen data, prompting an investigation by third-party experts and law enforcement. Systems remain offline, with no definitive timeline for restoration. https://securityaffairs.com/162910/cyber-crime/city-of-wichita-lockbit-ransomware.html
🥠 Stealing cookies: Researchers describe how to bypass modern authentication security research – Researchers detail bypassing modern authentication via MITM attack. https://cyberscoop.com/stealing-cookies-researchers-describe-how-to-bypass-modern-authentication/
🔐 Why Your VPN May Not Be As Secure As It Claims – Krebs on Security security research – Researchers reveal VPN vulnerability via rogue DHCP server attacks. https://krebsonsecurity.com/2024/05/why-your-vpn-may-not-be-as-secure-as-it-claims/
💸 Online Scams: Are These All Scams? Distinguishing the Legit from the Scam cybercrime – Sophisticated scammers create fake websites and emails, deceiving users. https://asec.ahnlab.com/en/65091/
🔑 Yubico bolsters authentication security with updated YubiKey 5 series devices security news – Yubico releases updated security keys with enhanced features. https://www.theverge.com/2024/5/7/24150918/yubico-5-7-firmware-update-security-key-yubikey-5
🔗 April 2024’s Most Wanted Malware: Surge in Androxgh0st Attacks and the Decline of LockBit3 security research – significant increase in AndroXgh0st malware attacks during April 2024, alongside a noticeable decrease in LockBit3.0 attacks, highlighting the shifting landscape of cybersecurity threats. https://blog.checkpoint.com/security/april-2024s-most-wanted-malware-surge-in-androxgh0st-attacks-and-the-decline-of-lockbit3/
🔍 New Case Study: The Malicious Comment security news – Malicious code hidden in 'Thank you' image compromised online shoppers. https://thehackernews.com/2024/05/new-case-study-malicious-comment.html
⛔ Stolen children’s health records posted online in extortion bid data breach – Children's health records from NHS Dumfries and Galloway published by cybercriminals for extortion. https://therecord.media/scotland-nhs-children-records-posted-extortion-ransomware
🧠 Back to the Hype: An Update on How Cybercriminals Are Using GenAI cybercrime – Cybercriminals continue to use generative AI, focusing on jailbreaking capabilities and emerging deepfake services for criminal activities. https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/back-to-the-hype-an-update-on-how-cybercriminals-are-using-genai
✈️ Boeing confirms attempted $200 million ransomware extortion attempt cybercrime – Boeing faced a $200 million ransomware demand from LockBit, part of a larger cyberattack. Boeing did not pay the ransom and the incident impacted its parts and distribution business. https://cyberscoop.com/boeing-confirms-attempted-200-million-ransomware-extortion-attempt/
🚔 FBI Warns US Retailers That Cybercriminals Are Targeting Their Gift Card Systems warning – FBI warns US retailers of a cybercriminal group targeting staff with phishing attacks to create fraudulent gift cards, highlighting the financial losses and sophisticated tactics used. https://www.tripwire.com/state-of-security/fbi-warns-us-retailers-cybercriminals-are-targeting-their-gift-card-systems
❤️🩹 Major health care system hobbled by ‘cyber incident’ cybercrime – Ascension health care system suffers a cyber incident causing disruptions to clinical operations, affecting medical services, patient records access, and necessitating manual documentation. Incident follows recent high-profile attacks in the healthcare industry, highlighting the need for cybersecurity standards. https://cyberscoop.com/major-health-care-system-hobbled-by-cyber-incident/
📢 Dell discloses data breach impacting millions of customers data breach – Dell revealed a data breach affecting millions of customers, exposing names, physical addresses, and hardware purchase data. Financial details and sensitive information were not compromised. https://securityaffairs.com/162942/cyber-crime/dell-data-breach-2.html
📱 Malicious Android Apps Pose as Google, Instagram, WhatsApp to Steal Credentials malware – Malicious Android apps impersonate popular services to trick users into installing them, then request extensive permissions to steal credentials and perform malicious activities, such as accessing contact lists, SMS messages, and launching phishing pages mimicking social media and financial services. https://thehackernews.com/2024/05/malicious-android-apps-pose-as-google.html
🪲 Google fixes fifth actively exploited Chrome zero vulnerability – Google patched the fifth zero-day vulnerability in Chrome this year, a use-after-free issue in the Visuals component, actively exploited in the wild, without disclosing details about the attacks. https://securityaffairs.com/162976/hacking/5th-chrome-zero-day-2024.html
😨 You've Been Breached: What Now? cyber defense – Breaches are inevitable in cybersecurity; after a breach, focus shifts to identifying the blast radius, providing temporary work credentials for affected employees, accountability at the executive level, and implementing incident response planning and a comprehensive cybersecurity strategy for recovery. https://www.darkreading.com/cyberattacks-data-breaches/you-have-been-breached-what-now
⚔️ MITRE attributes the recent attack to China security news – MITRE discloses security breach attributed to China-linked UNC5221. https://securityaffairs.com/162811/hacking/mitre-security-breach-china.html
🫢 RemcosRAT Distributed Using Steganography security research – RemcosRAT distributed using steganography technique, warns of malware infection risks. https://asec.ahnlab.com/en/65111/
🗣️ Talos discloses multiple zero-day vulnerabilities, two of which could lead to code execution vulnerability – Cisco Talos discloses three zero-day vulnerabilities, two allowing code execution. https://blog.talosintelligence.com/vulnerability-roundup-zero-days-may-8-2024/
🤌 Breaking down Microsoft’s pivot to placing cybersecurity as a top priority security news – Microsoft faced criticism over their security practices, prompting a new focus on cybersecurity as a top priority with six pillars. The announcement includes re-prioritizing efforts to enhance internal systems and respond to threats promptly. The new governance structure is designed to centralize security efforts and hold leadership accountable for progress. Despite past issues, this shift demonstrates a commitment to improving security practices and ensuring Microsoft products are a safe choice for users. https://doublepulsar.com/breaking-down-microsofts-pivot-to-placing-cybersecurity-as-a-top-priority-734467a8db01
⚙️ 21115: An Oracle VirtualBox LPE Used to Win Pwn2Own vulnerability – The exploit involved a bug in the VGA device heap memory, which could be triggered by setting specific values. Through a series of steps, the exploit gained increased VRAM access, disabled critical sections, achieved buffer overread and overflow, and executed arbitrary code, ultimately demonstrating control over the host system. https://www.thezdi.com/blog/2024/5/9/cve-2024-21115-an-oracle-virtualbox-lpe-used-to-win-pwn2own
🚗 GhostStripe attack haunts self-driving cars by making them ignore road signs security news – novel hack called “GhostStripe” that targets autonomous vehicles by manipulating road sign visibility to the vehicles' cameras, making the signs unrecognizable to the self-driving system and thus potentially leading to dangerous driving errors. https://www.theregister.com/2024/05/10/baidu_apollo_hack/
🥅 Protecting Networks from Opportunistic Ivanti Pulse Secure Vulnerability Exploitation cyber defense – Juniper Threat Labs is monitoring the Ivanti Pulse Secure authentication bypass and remote code execution vulnerabilities being exploited by Mirai botnet. https://blogs.juniper.net/en-us/security/protecting-your-network-from-opportunistic-ivanti-pulse-secure-vulnerability-exploitation
🐡 Unmasking Tycoon 2FA: A Stealthy Phishing Kit Used to Bypass Microsoft 365 and Google MFA security research – the Tycoon 2FA phishing kit, which exploits session cookies to bypass multifactor authentication for Microsoft 365 and Gmail, employing a business model via Telegram to sell phishing services and significantly impacting cybersecurity efforts. https://www.proofpoint.com/us/blog/email-and-cloud-threats/tycoon-2fa-phishing-kit-mfa-bypass
CISA Corner 🪫 CISA Advisory – alpitronic Hypercharger EV Charger vulnerability – Vulnerability in alpitronic Hypercharger EV charger allows attackers to disable the device, bypass payment, and access payment data due to the use of default credentials. Mitigations include changing default passwords, limiting network exposure, and implementing secure access methods. https://www.cisa.gov/news-events/ics-advisories/icsa-24-130-02
⚠️ #StopRansomware: Black Basta security news – The joint advisory from FBI, CISA, HHS, and MS-ISAC reveals details on Black Basta, a ransomware variant impacting critical infrastructure sectors, including Healthcare and Public Health, outlining TTPs and IOCs to assist organizations in protecting against Black Basta and other ransomware threats. https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-131a
🤹 ASD’s ACSC, CISA, and Partners Release Secure by Design Guidance on Choosing Secure and Verifiable Technologies https://www.cisa.gov/news-events/alerts/2024/05/09/asds-acsc-cisa-and-partners-release-secure-design-guidance-choosing-secure-and-verifiable
from Sirius
Prefácio de Albert Einstein sobre a introdução à Lucrécio.
Titus Lucretius Carus (c. 94 a.C. – c. 50 a.C.) era um poeta e filósofo epicurista romano que, em seu De rerum natura (Da Natureza das Coisas), descreveu o universo como a combinação do vazio e uma coleção de minúsculas partículas semelhantes a átomos em movimento perpétuo (seguindo os seus mestres Demócrito e Epicuro), com o diferencial de ter adicionado a elas um desvio imprevisível, chamado clinamen, que as leva a colidir e compor formas mais complexas.
Tal estrutura não permite a vida após a morte, apenas a disseminação do corpo e da alma de volta às partículas. O imperativo estabelecido por Lucrécio, seguindo os ensinamentos de Epicuro, era que o homem maximizasse o prazer e minimizasse a dor na única vida que lhe estava disponível. No universo de Lucrécio era impensável que os deuses, absortos nos seus próprios afazeres, tivessem algum interesse nos assuntos humanos. O homem era livre para seguir seu próprio caminho.
Einstein, em suas correspondências, realiza uma introdução ao pensamento de Lucrécio, a qual segue abaixo com as devidas vênias por eventual má tradução do idioma alemão:
Introdução a Lucrécio
PREFÁCIO
Para qualquer pessoa que não esteja totalmente imersa no espírito de nosso tempo, mas ocasionalmente se sinta como um espectador em relação ao seu mundo e especialmente à mentalidade intelectual dos contemporâneos, a obra de Lucrécio exercerá seu encanto. Aqui se vê como um homem dotado de interesse científico e especulativo, com sensibilidade e pensamento vivos, concebe o mundo, alguém independente que também não tem ideia dos resultados da ciência natural atual que nos são ensinados na infância, antes de podermos conscientemente ou criticamente enfrentá-los.
Deve causar uma profunda impressão a firme confiança que Lucrécio, como fiel discípulo de Demócrito e Epicuro, deposita na compreensibilidade, respectivamente, na conexão causal de todos os acontecimentos mundiais. Ele está firmemente convencido, a ponto de acreditar que pode até mesmo provar, que tudo se baseia no movimento regular de átomos imutáveis, aos quais ele não atribui outras qualidades além das geométrico-mecânicas. Diz-se que as qualidades sensoriais do calor, do frio, da cor, do cheiro e do sabor remontam aos movimentos dos átomos, assim como todos os fenômenos da vida. Ele pensa que a alma e o espírito são formados a partir de átomos particularmente leves, atribuindo (inconsistentemente) qualidades particulares da matéria a caracteres experienciais específicos.
Ele tem como objetivo principal do seu trabalho a libertação das pessoas do medo servil causado pela religião e pela superstição, que é nutrido e explorado pelos sacerdotes para seus próprios fins. Certamente ele se preocupa com isso. Mas ele parece ter sido motivado principalmente pela necessidade de convencer os seus leitores da necessidade da visão de mundo atomista-mecânica, mesmo que não ousasse dizê-lo abertamente aos seus leitores romanos, que eram provavelmente mais práticos. Sua admiração por Epicuro, pela cultura e pela língua grega em geral, que ele coloca bem acima do latim, é comovente. Os romanos devem ser elogiados por permitirem que isso fosse dito. Onde está a nação moderna que nutre e expressa tal nobre sentimento em relação a uma contemporânea? Os versos de Diels são tão naturais que se esquece que se está diante de uma tradução.
Berlim, junho de 1924.
Albert Einstein
Eventualmente editarei esse texto para acrescentar alguns trechos do Da Natureza das Coisas.
from Bruno Miguel
If you listen to online radio and prefer a client for the terminal, check this article on LinuxLinks.
#Linux #CLI #OnlineRadio
from 📰wrzlbrmpft's cyberlights💥
A weekly shortlist of cyber security highlights. The short summaries are AI generated! If something is wrong, please let me know!
🤖 CISA unveils guidelines for AI and critical infrastructure security news https://fedscoop.com/cisa-unveils-guidelines-for-ai-and-critical-infrastructure/
🔍 Watchdog reveals lingering Google Privacy Sandbox worries privacy https://go.theregister.com/feed/www.theregister.com/2024/04/29/uk_cma_google/
⚠️ Bewertungen entfernen lassen? Vorsicht vor entferno.at warning https://www.watchlist-internet.at/news/google-bewertungen-entfernen-lassen-vorsicht-vor-entfernoat/
🔒 UK becomes first country to ban default bad passwords on IoT devices security news https://therecord.media/united-kingdom-bans-defalt-passwords-iot-devices
🔓 FBCS data breach impacted 2M individuals data breach https://securityaffairs.com/162514/cyber-crime/fbcs-data-breach.html
😶 Russia Clones Wikipedia, Censors It, Bans Original security news – Russia clones Wikipedia to censor and ban original content. https://www.404media.co/russia-clones-wikipedia-censors-it-bans-original/
🐄 The UK beefs up smart home security by going after bad default passwords security news https://www.theverge.com/2024/4/29/24144325/uk-psti-password-requirements-network-connected-devices-iot-smart-home
📍 FCC Fines Major U.S. Wireless Carriers for Selling Customer Location Data – Krebs on Security privacy https://krebsonsecurity.com/2024/04/fcc-fines-major-u-s-wireless-carriers-for-selling-customer-location-data/
🔐 Apple's 'incredibly private' Safari not so private in Europe privacy – Apple's Safari browser in Europe exposed to privacy flaws due to third-party app store feature, leaking user activity and identifiers to approved marketplaces. Implementation lacks security measures, raising concerns about tracking. https://go.theregister.com/feed/www.theregister.com/2024/04/30/apple_safari_europe_tracking/
🚗 Carmakers lying about requiring warrants before sharing location data, Senate probe finds privacy – Senate probe finds automakers deceive customers by sharing driver location data without warrants, contradicting pledges, and misleading for years. Requested FTC investigation. Automakers store location data for years. Alliance for Automotive Innovation statement conflicts with findings. https://therecord.media/carmakers-lying-about-warrants-location-data
💸 UnitedHealth CEO confirms company paid $22 million ransom in heated Senate hearing security news – UnitedHealth Group paid ransom to BlackCat/AlphV gang post-ransomware attack. CEO admits multifactor authentication lapse. Senators criticize data restoration issues and impact on medical organizations. https://therecord.media/unitedhealth-ceo-testifies-senate-hearing
🌐 We can have a different web Blogpost – Reflections on the evolution of the web from an open space to commercialized walled gardens. Call for reclaiming the web's original spirit of innovation, authenticity, connection, and less surveillance. https://www.citationneeded.news/we-can-have-a-different-web/
🗝️ Microsoft launches passkey support for all consumer accounts security news – allowing face, fingerprint, PIN, or security key authentication across devices to streamline signing in without traditional passwords. https://www.theverge.com/2024/5/2/24147124/microsoft-passkeys-support-consumer-msa
🛡️ Organizations patch CISA KEV list bugs 3.5 times faster than others, researchers find security news https://therecord.media/kev-list-vulnerabilities-patched-significantly-faster
🕵️ Indonesia sneakily buys spyware, says Amnesty International security news – Amnesty International reveals Indonesia's purchase of spyware from various suppliers through intermediary companies, citing the lack of transparency and regulation in dual-use technology exports. https://go.theregister.com/feed/www.theregister.com/2024/05/03/amnesty_indonesia_surveillance/
👔 Microsoft ties executive pay to security following multiple failures and breaches security news – Microsoft faces severe criticism for security failures and breaches, including breaches by China and Russia-based hacking groups; response under scrutiny by lawmakers and regulators. Introduces 'Secure Future Initiative' and ties executive pay to security milestones, emphasizing robust security practices. https://arstechnica.com/information-technology/2024/05/microsoft-ties-executive-pay-to-security-following-multiple-failures-and-breaches/
💑 Dating apps kiss'n'tell all sorts of sensitive user info privacy – Most dating apps collect excessive user data, poor privacy practices revealed by Mozilla research. Grindr singled out for historically weak data protection. Concerns raised over user data sharing, AI integration, and privacy violations. https://www.theregister.com/2024/05/04/dating_apps_privacy_mozilla/
🛡️ Brokewell: do not go broke from new banking malware! malware – Brokewell, a dangerous mobile banking malware with device takeover capabilities. https://www.threatfabric.com/blogs/brokewell-do-not-go-broke-by-new-banking-malware
🔒 How we fought bad apps and bad actors in 2023 security news – Google Play's security measures in 2023. https://security.googleblog.com/2024/04/how-we-fought-bad-apps-and-bad-actors-in-2023.html
🔓 Multiple Brocade SANnav SAN Management SW flaws allow device compromise vulnerability https://securityaffairs.com/162473/uncategorized/brocade-sannav-flaws.html
🦠 Nearly 20% of Docker Hub Repositories Spread Malware & Phishing Scams security research – JFrog's security research team discovered nearly 20% of Docker Hub repositories hosting malicious content, ranging from spam to harmful entities like malware and phishing sites, driven by fake imageless repositories. Identified massive malicious campaigns targeting Docker Hub, leading to removal of 3.2 million suspicious repositories. https://jfrog.com/blog/attacks-on-docker-with-millions-of-malicious-repositories-spread-malware-and-phishing-scams/
💻 AWS S3 storage bucket with unlucky name nearly cost developer $1,300 security news – Developer's AWS S3 bucket with common name faces massive unauthorized requests due to an open-source tool, accumulating over $1,300 bill in one day. https://arstechnica.com/information-technology/2024/04/aws-s3-storage-bucket-with-unlucky-name-nearly-cost-developer-1300/
⚔️ Uncharmed: Untangling Iran's APT42 Operations security research – APT42 operations by Iranian state-sponsored threat actor with focus on enhanced social engineering, credential harvesting, cloud operations, and custom backdoors NICECURL and TAMECAT. Mandiant links APT42 to IRGC-IO and outlines their methods of stealing Microsoft, Yahoo, Google credentials. https://cloud.google.com/blog/topics/threat-intelligence/untangling-iran-apt42-operations/
🍯 Examining the Deception infrastructure in place behind code.microsoft.com security research – Microsoft repurposes the dangling subdomain code.microsoft.com into a honeypot to gather threat intelligence, simulating attacker interactions for research and protection. https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/examining-the-deception-infrastructure-in-place-behind-code/ba-p/4124464
🛡️ “Dirty stream” attack: Discovering and mitigating a common vulnerability pattern in Android apps security research – Microsoft identifies a path traversal vulnerability pattern in popular Android apps, facilitating arbitrary code execution and token theft, with potential disastrous consequences. https://www.microsoft.com/en-us/security/blog/2024/05/01/dirty-stream-attack-discovering-and-mitigating-a-common-vulnerability-pattern-in-android-apps/
🗽 State of Exploitation – A Peek into the Last Decade of Vulnerability Exploitation security research – Explores vulnerability trends from 2014 to 2023. Increase in known exploitation and POC exploits. https://vulncheck.com/blog/state-of-exploitation-a-decade
CISA Corner Microsoft SmartScreen Prompt https://www.cisa.gov/news-events/alerts/2024/04/30/cisa-adds-one-known-exploited-vulnerability-catalog GitLab Community and Enterprise Editions https://www.cisa.gov/news-events/alerts/2024/05/01/cisa-adds-one-known-exploited-vulnerability-catalog CERT/CC Reports R Programming Language Vulnerability https://www.cisa.gov/news-events/alerts/2024/05/01/certcc-reports-r-programming-language-vulnerability
While my intention is to pick news that everyone should know about, it still is what I think is significant, cool, fun... Most of the articles are in English, but some current warnings might be in German.
from Kevin Neely's Security Notes
The annual Verizon Data Breach Investigation Report is out, and along with it an accounting of the #cybersecurity compromise and data breach happenings for the past year. As always, it's filled with data analysis and some trending commentary from the previous DBIR report.
The following is a TL;DR summary generated using fabric by Daniel Miessler with some very minor editing.
This year, the 2024 DBIR reveals a significant rise in vulnerability exploitation and ransomware attacks, emphasizing the urgent need for enhanced cybersecurity measures.
from Bruno Miguel
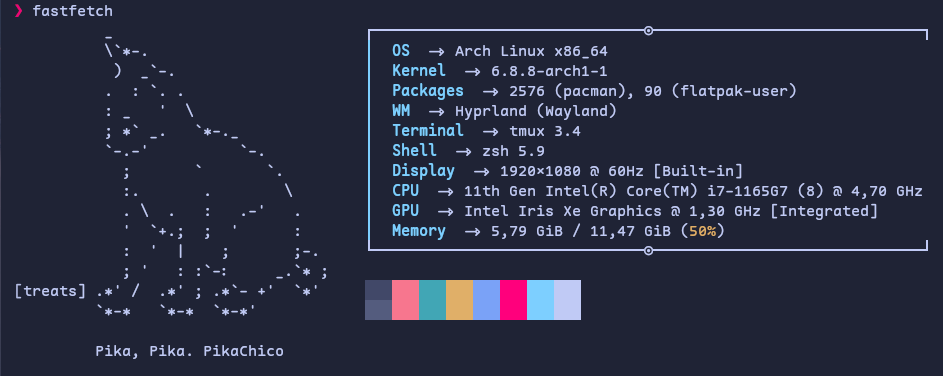
Neofetch is no more. The git repository for the venerable tool to show off the users' window manager configurations on /r/unixporn was archived and will no longer be maintained. Granted, it hadn't received a commit for around 3 years, so this is not unexpected. Thankfully, many tools of this kind abound in the FOSS world. One is Fastfetch, which is very similar to Neofetch but supposedly faster. Moments ago, I installed Fastfech and wasted a little bit of time configuring it. Why? Because.
The main difference between the two, from a user point of view, is that JSONC is used for Fastfetch's configuration. You can see all the options for the built-in modules on the schema present at the tool's repository or the documentation. You can also use my configuration below as a starting point.
{
"$schema": "https://github.com/fastfetch-cli/fastfetch/raw/dev/doc/json_schema.json",
"logo": {
"type": "file",
"source": "$HOME/.config/fastfetch/logo.txt"
},
"display": {
"separator": " -> "
},
"modules": [
{
"type": "custom",
"format": "┌────────────────────────────────────────────────────────────┐"
},
{
"type": "os",
"key": "│ OS"
},
{
"type": "kernel",
"key": "│ Kernel"
},
{
"type": "packages",
"key": "│ Packages",
},
{
"type": "wm",
"key": "│ WM",
},
{
"type": "terminal",
"key": "│ Terminal",
},
{
"type": "shell",
"key": "│ Shell"
},
{
"type": "display",
"key": "│ Display"
},
{
"type": "cpu",
"key": "│ CPU",
},
{
"type": "gpu",
"key": "│ GPU",
},
{
"type": "memory",
"key": "│ Memory",
},
{
"type": "swap",
"key": "│ Swap"
},
{
"type": "custom",
"format": "└────────────────────────────────────────────────────────────┘"
},
"break",
{
"type": "colors"
}
]
}
If you want something different, there are several options, such as Nitch, Pfetch, Catnip, and Meowfetch. I'm the maintainer for the meowfetch-git package on Arch Linux's AUR, and I recommend it if you want to see a kitty every time you display your system info on the terminal.
via It's FOSS
#Neofetch #Fastfetch #UnixPorn #Linux #FOSS
from 📰wrzlbrmpft's cyberlights💥
A weekly shortlist of cyber security highlights. The short summaries are AI generated! If something is wrong, please let me know.
A little late this week and a little shorter, but with some work put into the summary-thingy. Enjoy.
🔐 Firstyear's blog – Passkeys – A shattered dream privacy – Author expresses frustration with the direction of Passkeys and issues with Webauthn standards, emphasizing the importance of password managers. https://fy.blackhats.net.au/blog/2024-04-26-passkeys-a-shattered-dream/
🚗 How G.M. Tricked Millions of Drivers Into Being Spied On (Including Me) privacy – G.M. collected driving data from OnStar users, shared with insurers. https://www.nytimes.com/2024/04/23/technology/general-motors-spying-driver-data-consent.html?unlocked_article_code=1.m00.gIzH.YdQ-yszzdzq6
⚠️ A flaw in the Forminator plugin impacts hundreds of thousands of WordPress sites vulnerability – Forminator plugin allows unrestricted file uploads, other vulnerabilities. https://securityaffairs.com/162113/security/forminator-wordpress-plugin-flaws.html
🔒 Europol asks tech firms, governments to get rid of E2EE privacy – Europol calls for end to E2EE to combat crimes, sparking debate on privacy versus law enforcement access. https://www.theregister.com/2024/04/22/europol_becomes_latest_cop_shop/
🛡️ Hackers infect users of antivirus service that delivered updates over HTTP cybercrime – Hackers exploit eScan antivirus service for five years via MitM attack to deliver malware to end users. https://arstechnica.com/security/2024/04/hackers-infect-users-of-antivirus-service-that-delivered-updates-over-http/
⚕️ Nurses Protest 'Deeply Troubling' Use of AI in Hospitals security news – Nurses protest AI implementation in healthcare for potential negative impact on patient care and job roles. https://www.404media.co/nurses-protest-ai-automation/
🔒 Ring to pay $5.6M to settle claims of poor privacy practices privacy – The FTC fines Ring for poor privacy practices, leading to unauthorized access to customer cameras by cybercriminals and rogue employees. https://www.theregister.com/2024/04/25/ring_ftc_settlement/
📱 Flaws in Chinese keyboard apps expose smartphones to snoops privacy – Chinese keyboard apps, including major manufacturers' offerings, leak keystrokes due to weak encryption potentially exposing over 780 million smartphone users to surveillance. https://www.theregister.com/2024/04/26/pinyin_keyboard_security_risks/
🍷 Sweden’s liquor supply severely impacted by ransomware attack cybercrime – A ransomware attack on Swedish logistics company Skanlog severely impacts Sweden's liquor supply. https://securityaffairs.com/162333/cyber-crime/swedens-liquor-supply-ransomware-attack.html
🔒 Discord Shuts Down ‘Spy Pet’ Bots That Scraped, Sold User Messages privacy https://www.404media.co/discord-shuts-down-spy-pet-bots-that-scraped-sold-user-messages/
⚠️ Experts warn of malware campaign targeting WP vulnerability – A critical SQL injection vulnerability in the WordPress Automatic plugin allows attackers to inject backdoors and compromise websites. Admins are urged to update immediately. https://securityaffairs.com/162364/hacking/wordpress-automatic-critical-flaw.html
🔒 Okta warns of unprecedented scale in credential stuffing attacks on online services https://securityaffairs.com/162464/hacking/okta-warned-spike-credential-stuffing-attacks.html
🔒 How to Remove Personal Information From Data Broker Sites privacy – Data brokers, like Acxiom and Epsilon, collect personal information for marketing purposes. Advises visiting each broker's site, create an account, locate your information, and request removal to safeguard privacy. Opting out may vary require annual repetition. https://www.mcafee.com/blogs/tips-tricks/how-to-remove-personal-information-from-data-broker-sites/
🔒 (The) Postman Carries Lots of Secrets ◆ Truffle Security Co. security news – Postman, known for hosting a vast collection of public APIs, has become a major source of leaked secrets with over 4,000 live credentials exposed. https://trufflesecurity.com/blog/postman-carries-lots-of-secretsf
🐍 CERT.at Double Agents and User Agents: Navigating the Realm of Malicious Python Packages malware – Malicious Python packages act as double agents, tricking users to build grabbers that collect data for nefarious purposes. https://cert.at/en/blog/2024/4/double-agents-and-user-agents-navigating-the-realm-of-malicious-python-packages
⚔️ M-Trends 2024: Our View from the Frontlines security research – Mandiant Consulting's M-Trends report highlights increased attacker evasion tactics and improved defender detection, emphasizing the need for ongoing vigilance in cybersecurity. https://cloud.google.com/blog/topics/threat-intelligence/m-trends-2024/
🔍 Distribution of Infostealer Made With Electron malware – Infostealer malware strain created with Electron framework; evades detection with NSIS installer format. https://asec.ahnlab.com/en/64445/
🪝 Unplugging PlugX: Sinkholing the PlugX USB worm botnet security research – Sophos and Sekoia sinkhole PlugX worm botnet to control its activities and explore remote system disinfection methods. https://blog.sekoia.io/unplugging-plugx-sinkholing-the-plugx-usb-worm-botnet/
📵 A Briefing on SIM Hijacking cybercrime – SIM hijacking: stealing phone numbers for cryptocurrency theft and account takeovers. https://intel471.com/blog/a-briefing-on-sim-hijacking
🦮 Microsoft Security – Guidance for Incident Responders cyber defense https://cdn-dynmedia-1.microsoft.com/is/content/microsoftcorp/microsoft/final/en-us/microsoft-brand/documents/IR-Guidebook-Final.pdf
🔐 The private sector probably isn’t coming to save the NVD security news – Major backlogs in U.S. National Vulnerability Database prompt potential solutions from government and private sector https://blog.talosintelligence.com/threat-source-newsletter-april-25-2024/
🧠 Microsoft Deleted Its LLM Because It Didn’t Get a Safety Test, But Now It’s Everywhere security news – Microsoft releases powerful language model, WizardLM 2, without safety testing, leading to unintended spread on the internet. https://www.404media.co/microsoft-deleted-its-llm-because-it-didnt-get-a-safety-test-but-now-its-everywhere/
CISA Corner Cicso ASA & CrushFTP added to KEV https://www.cisa.gov/news-events/alerts/2024/04/24/cisa-adds-three-known-exploited-vulnerabilities-catalog Microsoft Print Spooler PEV added to KEV https://www.cisa.gov/news-events/alerts/2024/04/23/cisa-adds-one-known-exploited-vulnerability-catalog
While my intention is to pick news that everyone should know about, it still is what I think is significant, cool, fun... Most of the articles are in English, but some current warnings might be in German.
from Bruno Miguel
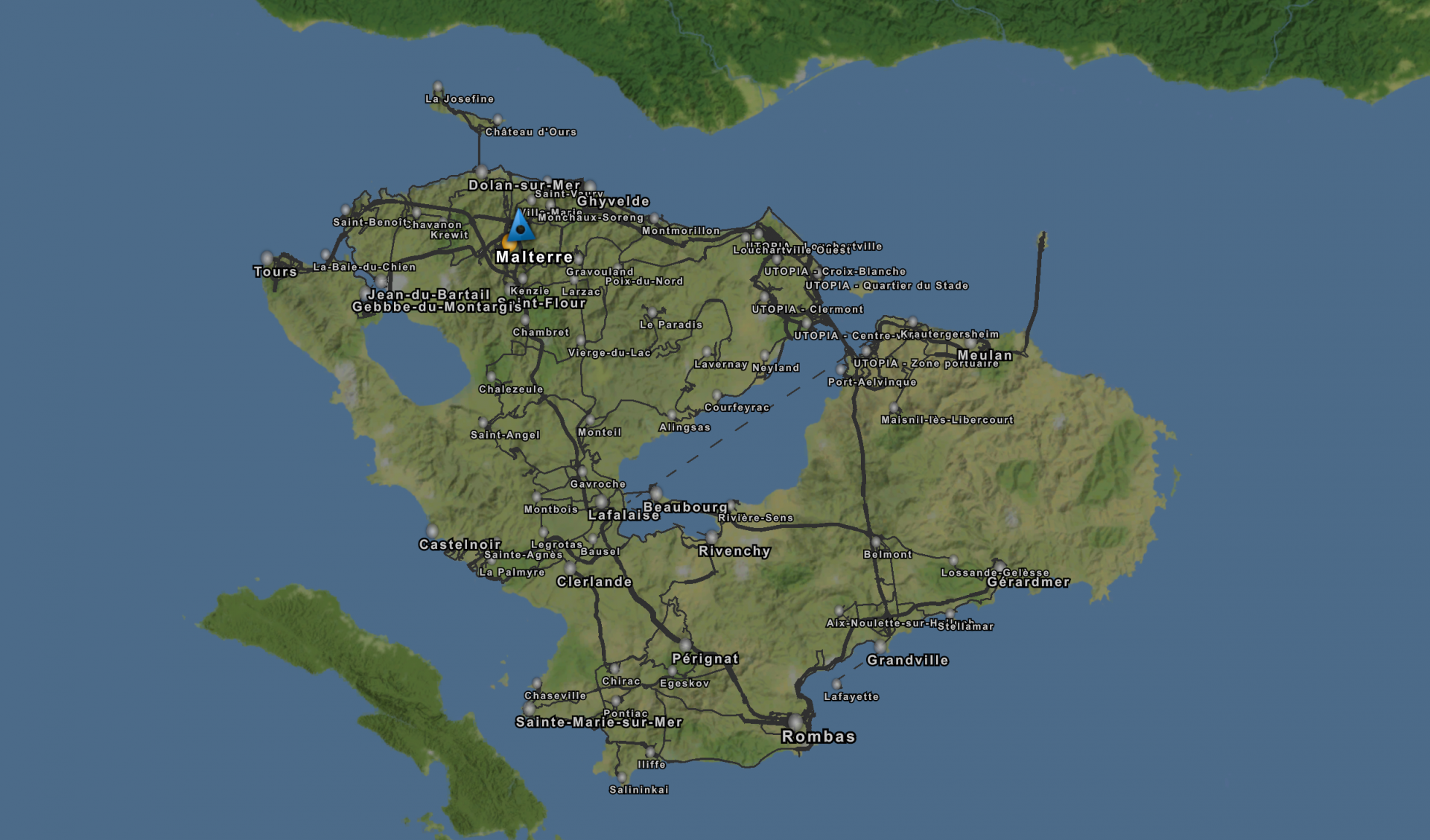 Image from the Grand Utopia website. All rights reserved to the project
Image from the Grand Utopia website. All rights reserved to the project
I uninstalled Euro Truck Simulator 2 (ETS2) a few weeks ago. I needed the space to install another game and try it out. That game was cool but not as good as ETS2, so I replaced it with the truck driving simulator. However, after watching a streamer use it, I added the Grand Utopia mod.
Grand Utopia is a map mod of a fictional island, partially inspired by the game's French map. The best thing about it is it uses a 1:1 scale, unlike the official game maps, which means a trip takes around the same time as it would in real life for its distance. The scenery is also well made but uses more graphic elements, so expect it to utilize more resources.
I've been playing with this mod for over a week and enjoy it very much. The new places to unlock, the beautiful sceneries, and the 1:1 scale add to a pleasant gaming experience. I cannot recommend it enough.
If you want to try Grand Utopia, there's one thing you need to do: create a new profile. It won't work with your current profiles and will even crash the game if you try to force it on an existing one.
#Linux #LinuxGaming #ETS2 #EuroTruckSimulator2 #Gaming
from 📰wrzlbrmpft's cyberlights💥
A weekly shortlist of cyber security highlights. The short summaries are AI generated! If something is wrong, please let me know.
Highlight 🚨 Erneut Phishing-Mails im Namen der ÖGK im Umlauf! https://www.watchlist-internet.at/news/erneut-phishing-mails-im-namen-der-oegk-im-umlauf/
🐢 PuTTY vulnerability vuln-p521-bias vulnerability https://www.chiark.greenend.org.uk/~sgtatham/putty/wishlist/vuln-p521-bias.html
🦦 Fake cheat lures gamers into spreading infostealer malware security news https://www.bleepingcomputer.com/news/security/fake-cheat-lures-gamers-into-spreading-infostealer-malware/
🤖 Liberals accuse Conservatives of using AI for amendments to jobs bill as votes loom security news – using AI for unconstructive bill amendments https://www.cbc.ca/news/politics/sustainable-jobs-bill-amendments-1.7171414
💻 UPDATED: Ready or Not Developer Has 4TB Of Data Stolen Including Full Source Code data breach https://insider-gaming.com/ready-or-not-developer-has-4tb-of-data-stolen-including-full-source-code/
🌐 UNDP Investigates Cyber-Security Incident data breach – HR and procurement data stolen https://www.undp.org/speeches/undp-investigates-cyber-security-incident
🔑 Advanced Phishing Kit Adds LastPass Branding for Use in Phishing Campaigns warning – phishing campaign with Voice Phishing (Vishing) https://blog.lastpass.com/posts/2024/04/advanced-phishing-kit-adds-lastpass-branding-for-use-in-phishing-campaigns
🔐 Delinea releases Secret Server patches for critical vuln vulnerability – critical https://www.theregister.com/2024/04/15/delinea_secret_server_patch/
🔒 Roku switches on 2FA for all following latest security snafu *security news – after two incidents led to unauthorized access * https://www.theregister.com/2024/04/15/roku_2fa_for_everyone/
🛂 MGM sues to block FTC investigation of its data security security news – questioning the constitutionality of the agency's requests. https://therecord.media/mgm-sues-ftc-block-investigtion-data-security
🕵️ A Spy Site Is Scraping Discord and Selling Users’ Messages privacy – Spy Pet, an online service, selling access to users' messages, voice channel activity, and more for $5. https://www.404media.co/a-spy-site-is-scraping-discord-and-selling-users-messages/
🧢 House passes bill to limit personal data purchases by law enforcement, intelligence agencies mycat: security news privacy – “Fourth Amendment Is Not For Sale Act” to limit government purchases of personal data without a court order. https://cyberscoop.com/house-passes-4th-amendment-is-not-for-sale-act/
🤌 EU tells Meta it can't paywall privacy privacy – Meta maintains its subscription model complies with EU laws, while privacy groups argue against 'fake choice' practices, citing GDPR violations. https://www.theregister.com/2024/04/18/eu_meta_subscription_privacy/
🏫 Kaspersky Study: Devices Infected With Data-Stealing Malware Increased by 7 Times Since 2020 security research https://www.techrepublic.com/article/data-stealing-malware-study/
👥 Microsoft’s VASA-1 can deepfake a person with one photo and one audio track security news https://arstechnica.com/information-technology/2024/04/microsofts-vasa-1-can-deepfake-a-person-with-one-photo-and-one-audio-track/
🛡️ “Totally Unexpected” Package Malware Using Modified Notepad++ Plugin malware https://asec.ahnlab.com/en/64106/
⚔️ Leaked LockBit builder in a real-life incident response case security research – Analysis of LockBit builder in ransomware incident response https://securelist.com/lockbit-3-0-based-custom-targeted-ransomware/112375/
👁️ Entra IDs “Banned Password Lists”: password spraying optimizations and defenses security research https://www.synacktiv.com/en/publications/entra-id-banned-password-lists-password-spraying-optimizations-and-defenses
⚙️ Creating Payloads with ScareCrow to Mimic Reputable Sources and Bypass Anti-Virus hacking write-up https://infosecwriteups.com/creating-payloads-with-scarecrow-to-mimic-reputable-sources-and-bypass-anti-virus-01196cac741e
🍵 Shostack + Friends Blog > CSRB Report on Microsoft security news – An in-depth analysis of the CSRB report on Microsoft's intrusion. https://shostack.org/blog/csrb-report-on-microsoft/
⚖️ Warrantless spying powers extended to 2026 with Biden’s signature security news https://therecord.media/fisa-section-702-bill-biden-signature
🚄 Russia is trying to sabotage European railways, Czech minister said security news https://securityaffairs.com/161899/cyber-warfare-2/russia-sabotage-european-railways-czech.html
⏳ What’s the deal with the massive backlog of vulnerabilities at the NVD? security news – unanalyzed vulnerabilities, impacting patch management efforts and leading to delays in severity score assignments. https://blog.talosintelligence.com/nvd-vulnerability-backlog-the-need-to-know/
🪱 Unearthing APT44: Russia’s Notorious Cyber Sabotage Unit Sandworm security research https://cloud.google.com/blog/topics/threat-intelligence/apt44-unearthing-sandworm/
🥀 Critical CrushFTP zero-day exploited in attacks in the wild vulnerability https://securityaffairs.com/162067/hacking/crushftp-zero-day-exploited.html
CISA Corner Oracle Releases Critical Patch Update Advisory for April 2024 https://www.cisa.gov/news-events/alerts/2024/04/18/oracle-releases-critical-patch-update-advisory-april-2024 Cisco Releases Security Advisories for Cisco Integrated Management Controller https://www.cisa.gov/news-events/alerts/2024/04/19/cisco-releases-security-advisories-cisco-integrated-management-controller
While my intention is to pick news that everyone should know about, it still is what I think is significant, cool, fun... Most of the articles are in English, but some current warnings might be in German.
from Bruno Miguel
I have fibromyalgia, a hell that began almost four years ago. During the first two years, more or less, I read a lot of studies. Still, none got me genuinely excited. That is until a team in Sweden decided to see if the syndrome has an autoimmune origin. The first part of their investigation points to that, and there was subsequent Research from another team that also showed solid evidence of this hypothesis being correct. The second part of the Swede's is still pending.
As far as I know, that's it for Research. A team or even two might be doing work around fibromyalgia, but publishing it will probably take a while. Even after that, assuming the identification of the syndrome's origin and the development of an effective treatment, it will take even more time to adjust the current shitty therapies available that fail miserably at keeping the pain at bay or at least at non-hellish levels.
Every day, the hope of getting access to an effective treatment for fibromyalgia during my lifetime fades away, little by little.
#Health #Fibromyalgia #ChronicPain #Research
from 📰wrzlbrmpft's cyberlights💥
A weekly shortlist of cyber security highlights. The short summaries are AI generated! If something is wrong, please let me know!
🚫 Help us to take down the parasite website security news – Malicious site impersonates Notepad++ for profit, containing deceptive ads. https://notepad-plus-plus.org/news/help-to-take-down-parasite-site/
⚠️ Vorsicht vor kostenlosen Diensten zur Anpassung und Veränderung von Dateien warning – Vorsicht vor kostenlosen Dateikonvertierungsdiensten, die in Abofallen locken. https://www.watchlist-internet.at/news/vorsicht-vor-kostenlosen-diensten-zur-anpassung-und-veraenderung-von-dateien/
📑 Messenger-Matrix: Großes Update, zwei neue Messenger (Line, Viber) und neue Kategorien privacy https://www.kuketz-blog.de/messenger-matrix-grosses-update-zwei-neue-messenger-line-viber-und-neue-kategorien/
🦇 BatBadBut flaw allowed an attacker to perform command injection on Windows vulnerability – RyotaK discovered the 'BatBadBut' vulnerability affecting multiple programming languages, permitting command injection in Windows. https://securityaffairs.com/161785/security/batbadbut-flaw-programming-languages.html https://kb.cert.org/vuls/id/123335
🤖 Chinese hackers are using AI to inflame social tensions in US, Microsoft says cybercrime – China uses AI to spread disinformation, specifically targeting elections. https://therecord.media/china-ai-influence-operations
📞 How to Protect Yourself (and Your Loved Ones) From AI Scam Calls security news – avoid falling for AI scam calls impersonating loved ones. https://www.wired.com/story/how-to-protect-yourself-ai-scam-calls-detect/
❤️🩹 U.S. Department of Health warns of attacks against IT help desks security news – Sophisticated attacks target healthcare IT help desks using social engineering. https://securityaffairs.com/161566/hacking/healthcare-it-help-desks-attacks.html
💰 Company Offering $30 Million for Android, iOS, Browser Zero-Day Exploits security news https://www.securityweek.com/company-offering-30-million-for-android-ios-browser-zero-day-exploits/
🔍 It Was Not Me! Malware-Initiated Vulnerability Scanning Is on the Rise security research – Increasing trends in malware-initiated scanning attacks against networks. https://unit42.paloaltonetworks.com/malware-initiated-scanning-attacks/
🏥 Hospital websites share visitors' data with Google, Meta privacy – Research reveals that 96% of non-federal acute care hospitals' websites transmit user data to third parties without privacy policies, posing risks to visitors and hospitals. Tracking technologies expose data to tech giants like Google, Meta, Adobe, and data brokers. https://www.theregister.com/2024/04/11/hospital_website_data_sharing/
🍏 Apple swaps 'state-sponsored' lingo for 'mercenary spyware' security news – Apple shifts attributing attacks to broadly categorizing them, highlighting the difficulty in identifying perpetrators of sophisticated digital threats. https://www.theregister.com/2024/04/12/apple_mercenary_spyware/
💸 Change Healthcare faces another ransomware threat—and it looks credible cybercrime – Change Healthcare faces a complex ransomware situation, with ransomware groups AlphV and RansomHub involved. https://arstechnica.com/security/2024/04/change-healthcare-faces-another-ransomware-threat-and-it-looks-credible/
⚠️ Crooks manipulate GitHub's search results to distribute malware malware – techniques like automatic updates and fake stars to boost visibility. https://securityaffairs.com/161792/cyber-crime/githubs-search-results-distribute-malware.htmlf
🦫 Why CISA is Warning CISOs About a Breach at Sisense security news https://krebsonsecurity.com/2024/04/why-cisa-is-warning-cisos-about-a-breach-at-sisense/
🫦 Vulnerabilities Identified in LG WebOS vulnerability – Bitdefender discovers vulnerabilities in LG WebOS exposing devices to remote attacks. https://www.bitdefender.com/blog/labs/vulnerabilities-identified-in-lg-webos/
⚔️ Confidential VMs Hacked via New Ahoi Attacks security research – New Ahoi attacks target confidential VMs using malicious interrupts. https://www.securityweek.com/confidential-vms-hacked-via-new-ahoi-attacks/
🛡️ Microsoft fixes two Windows zero-days exploited in malware attacks vulnerability – Microsoft patches actively exploited zero-days in April 2024 Patch Tuesday. https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-two-windows-zero-days-exploited-in-malware-attacks/
🔍 Zero Day Initiative — The April 2024 Security Updates Review security news – Zero Day Initiative review of April 2024 security updates by Adobe and Microsoft. https://www.zerodayinitiative.com/blog/2024/4/9/the-april-2024-security-updates-review
💳 VISA PUBLIC Biannual Threats Report – A Payment Ecosystem Report by Visa Payment Fraud Disruption security news – Visa report highlights evolving, advanced fraud tactics and ransomware threats. https://usa.visa.com/content/dam/VCOM/regional/na/us/run-your-business/documents/pfd-biannual-threats-report-december-2023.pdf
🔑 Microsoft left internal passwords exposed in latest security blunder security news – Microsoft exposed internal passwords on open server to the internet. https://www.theverge.com/2024/4/10/24126057/microsoft-azure-server-internal-passwords-exposed-cybersecurity
🛡️ Credit Card Skimmer Hidden in Fake Facebook Pixel Tracker security research – Attackers embed credit card skimmer in fake Facebook Pixel script to steal sensitive information from checkout pages. https://blog.sucuri.net/2024/04/credit-card-skimmer-hidden-in-fake-facebook-pixel-tracker.html
🛡️ CISA emergency directive tells agencies to fix credentials after Microsoft breach security news – CISA issues emergency directive for federal agencies to reset passwords by April 30 and identify affected email correspondence due to security risks. https://cyberscoop.com/cisa-emergency-directive-tells-agencies-to-fix-credentials-after-microsoft-breach/
🔪 Awkward Adolescence: Increased Risks Among Immature Ransomware Operators security research – Contrasting mature ransomware groups with less sophisticated, riskier ones. https://www.guidepointsecurity.com/blog/awkward-adolescence-increased-risks-among-immature-ransomware-operators/
CISA Corner KEV – Palo Alto – CVSS 10 https://www.cisa.gov/news-events/alerts/2024/04/12/palo-alto-networks-releases-guidance-vulnerability-pan-os-cve-2024-3400 KEV – D-Link NAS https://www.cisa.gov/news-events/alerts/2024/04/11/cisa-adds-two-known-exploited-vulnerabilities-catalog Siemens https://www.cisa.gov/news-events/alerts/2024/04/11/cisa-releases-nine-industrial-control-systems-advisories Citrix Xen https://www.cisa.gov/news-events/alerts/2024/04/12/citrix-releases-security-updates-xenserver-and-citrix-hypervisor Juniper https://www.cisa.gov/news-events/alerts/2024/04/12/juniper-releases-security-bulletin-multiple-juniper-products Microsofts BULK! https://www.cisa.gov/news-events/alerts/2024/04/09/microsoft-releases-april-2024-security-updates Adobe – more or less ALL https://www.cisa.gov/news-events/alerts/2024/04/09/adobe-releases-security-updates-multiple-products-0 Fortinet https://www.cisa.gov/news-events/alerts/2024/04/09/fortinet-releases-security-updates-multiple-products
While my intention is to pick news that everyone should know about, it still is what I think is significant, cool, fun... Most of the articles are in English, but some current warnings might be in German.
from stndinq
Read more...from Kevin Neely's Security Notes
I always loved Lesley Carhart's blog post on packing for hacker conferences and referred to it many times while prepping for #DEFCON , #BSides, other cons, and even general travel. As time has gone by, I've developed a three-tier system that kind of builds on itself for longer and more involved travel. The general ideaidea is that
The most basic level of the tech travel stack I've created is what I call “The Weekender”. it's meant for being out and about all day long or for short weekend getaways. As such, the requirements are basically: 1. Take up little room, being able to fit in any backpack or even a sling bag. 2. be able to charge the devices I'm likely to carry, from ear buds to a laptop. 3. Plan for extended periods away from a power source.
![]() image 1: Tier 1 go bag – The Weekender with a backup battery, USB-C to USB-C cable, USB-A to micro-USB cable, and USB-C adapter. Small, ready to go, and easy to drop into any bag.
image 1: Tier 1 go bag – The Weekender with a backup battery, USB-C to USB-C cable, USB-A to micro-USB cable, and USB-C adapter. Small, ready to go, and easy to drop into any bag.
In order to address these simple requirements, I realized I needed to be able to provide power to USB-C and micro-USB devices, for a laptop, I need a bit more oomph, so the adapter can deliver enough power to charge a laptop battery. Limited by the space requirements, I went with a 33W charger that can absolutely charge a laptop, but it will not keep up with power consumption under load. This means that if I'm going to be working all day on the laptop, I'm going to need to move up to the next tier.
Note that all cables can transfer data. For versatility, I don’t mess with power-only cables. – 1x USB-A to microUSB cable – 3ft. – 1x 5ft. USB-C to USB-C cable – This is the minimum length you want to ensure your phone can reach the bed when charging
Converters extend the utility and versatility of the other equipment – USB micro female to USB-C male. This gives me a third USB-C cable
![]() Image 2: Zipped Weekender Go-bag and its contents in detail
Image 2: Zipped Weekender Go-bag and its contents in detail
from critic
Che poi con la doccia alla sera si risparmia tempo la mattina... certo se poi quel tempo lo usi per pulire le cacche dei gatti allora torniamo al punto di partenza.
from critic
Non funziona con la app di Writefreely. Sono un po’ deluso. Nonostante ciò proverò ad usarlo via browser.